By Yamila Levalle
An air gap, air wall or air gapping is a network security measure applied to on one or more computers to ensure that they are physically isolated from unsecured networks, such as the public internet or an unsecured local area network. Basically it means a device or group of devices that have no network interfaces connected to other unsecure networks.
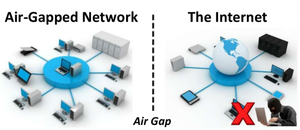
Over the years, many networks in many different verticals from governments, military, financial services, nuclear power plants and industrial manufacturing, to name a few, have been so-called вАЬair gapped.вАЭ Older ICS systems, many of which are still in use today, were built without cyber security in mind. The internet as we know it today did not exist, OT and internal IT systems were completely isolated from each other, and no one foresaw any reason for them to ever connect.
However, as organizations embrace digital transformation, OT and IT are converging and the commonly held belief that ICS/SCADA systems are immune to cyber attacks because they are disconnected from the Internet and the corporate network by an air gap, is no longer true or feasible in an interconnected world.
In theory, an air gap sounds like a good strategy. In practice, things are never that simple. Even in cases where an organization has taken every measure possible to isolate their ICS network and disconnect it from the outside world, we have seen cyber threats compromise the perimeter.
Sure you can simply unplug the connection between the control system and the business network and you have an air gap. Then one day:
- You get new logic from your engineering consultant addressing a design flaw that has been causing your company considerable downtime
- Adobe sends you a software update for a critical vulnerability in the PDF Reader your staff uses to view operational manuals
- Your lab group sends a process recipe that will improve product quality
The list keeps growing: patches for your computer operating systems, remote support and system software, you canвАЩt ignore them all.
So what do you do? Maybe you load some files onto a USB drive and carry that onto the plant floor. But isnвАЩt that how Stuxnet spread? Or maybe putting everything onto a laptop is the solution, but what if the laptop is infected? A serial line and a modem, but isnвАЩt that how the Slammer worm got into a number of control systems?
As much as we want to pretend otherwise, modern control systems need electronic information from the outside world. Severing the network connection with an air gap simply spawns new pathways.
Is the ICS system really air gapped?
The first question we ask ourselves when we perform air gapped systems assessments is: Is the ICS system or network really air gapped? The most common danger is to assume that air gapped networks arenвАЩt connected to the internet or other insecure networks. In reality, a surprising number actually do have connections that the IT staff misses or doesnвАЩt realize poses a threat.
Assessments typically find that an environment is never completely air gapped. Usually find evidence of unsanctioned external connections created by control engineers, most often for non-threatening, non-malicious reasons. These undocumented, unapproved network connections are usually created to ease an engineerвАЩs system maintenance and/or troubleshooting responsibilities to avoid from having to sneakernet a file or program to the control environment. Most of the time, these are only set up to provide short term relief, but what happens is that connections forget to be torn down, leaving the air gapped network wide open to other communication channels where behavior tends to lend itself to the malicious kind.
Common oversights with air gapping include: dual-homed computers and servers, legacy connections, backup connections, modems and wireless networks being set up by contractors, maintenance, or control engineers to transfer data in or out of the air gapped networks. Remote access for vendors and contractors, also is a significant and growing problem.
Air Gap Attacks
But even with a strict air gap in place, there are multiple ways for attackers to perform the initial infection and compromise an air gapped machine or network:
INFECTED MEDIA
The most common method is to infect a USB drive (or other removable media) which a contractor or employee is likely to connect to the secure device. This is how the Stuxnet malware was able to disrupt IranвАЩs nuclear program. Other real-world examples of malware jumping the air gap by first infecting USBs include вАЬAgent.BTZ,вАЭ вАЬSymonLoader,” вАЬRain Maker,вАЭ вАЬBrutal KangarooвАЭ and вАЬCottonmouth.вАЭ
COMPROMISED USERS AND MILICIOUS INSIDERS
Attackers could also utilize insiders within the facility, from engineers to executives, in order to conduct malicious operations. These may be insiders who are actually compromised, but more commonly, this involves insiders whose personal devices and/or corporate accounts have been compromised, allowing the attacker to insert malware targeted at devices and systems within the protected environment. Note that devices outside of the protected environment typically have far fewer network, operational, or physical security protections. Blackmail and bribery also are risks which need to be considered.
SUPPLY CHAIN ATTACKS
Another way to compromise an air-gapped system is to вАЬpre-penetrateвАЭ it before it ends up in the air gap by sabotaging its supply chain. ItвАЩs not unusual for an advanced attacker to study their victim and determine their technical infrastructure. Then the attacker can go after the suppliers to hide booby traps in the hardware or software.¬†There are several known cases of attackers hiding malware or secret backdoors in software libraries that are later implemented into production applications. The attack against the Ukrainian power grid involved compromising a third-party software package used by the utility. The developer of the software was compromised by the attackers, when the updated software package was distributed to the utility, the backdoor was installed for later use.
Outbound / Inbound Channels
But assuming the mission of the attackers isnвАЩt destruction or ransomware, after the initial infection they need an outbound channel to get the stolen data out and, if possible, also an inbound channel to send commands and updates to the compromised devices.
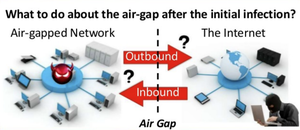
If the attackers used a USB drive for the initial infection, they could use the same method to get data out. But, attackers canвАЩt always count on an insider or someone else to unknowingly carry a USB with the data back out of a facility.
Attackers can also try to get access to the built-in communication interfaces the compromised computer encloses e.g. Wi-Fi, Bluetooth or GSM adapters. If one of these interfaces is present and can be enabled, they could set-up a fake base-station or router to start communicating with the compromised computer. Nevertheless, in sensitive environments, these type of interfaces are generally removed.
Luckily for the attackers, there are many ways of sending information over a distance. Information theory postulates that anything that you can cause to vary can be used to transmit information. As long as both sides of a conversation can interpret the message, lots of things can be used as a transmission medium.
The attackers are already in control of the air gapped computer, so they can encode signals in any manner they choose. They can then place a receiving device to make contact over a channel that can propagate across the air gap. The receiving device can be nothing more than an ordinary smartphone running the attackerвАЩs decoder software. This leaves a lot of possibilities for exfiltration.
POSSIBLE OUTBOUND / INBOUND CHANNELS
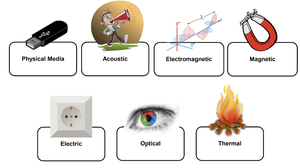
- Acoustic: Computer speakers can easily produce sound at levels inaudible to human hearing, so they can be used as an outbound and an inbound channel. Attackers can also use microphones, the computer fan or the hard drive actuator arm to transmit data.
- Optical: Optical covert channels are methods of exfiltrating data in a way undetectable to the human eye. Computer and peripherals (e.g. keyboard) are equipped with light indicators, attackers can covertly leak sensitive data from air gapped networks for example on вАШblinksвАЩ or on screen brightness changes.¬†If smart light sources (e.g. network controlled smart light bulbs) can be controlled by one of the compromised computers, they can also be used as a communication channel. On the other side, a light sensor or a video camera can be used to receive the signals.
- Thermal: Computers are emitting heat from CPU, GPU, HDD and are equipped with built-in thermal sensors. Attackers could use temperature as a communication channel, encoding data in temperature changes. Also, if the attackers can control the air conditioning and heating system of the room in which the compromised computer is, this computer can then monitor the temperature reported by its internal sensors and retrieve data, resulting in a very low bandwidth covert channel.
- Electric: A malicious code running on a compromised computer can control the power consumption of the system by intentionally regulating the CPU utilization. Attackers can use it as an outbound channel modulating, encoding, and transmitting data on top of the current flow fluctuations.
- Electromagnetic: Electric current in a wire produces an electromagnetic field. The electromagnetic field depends on the current pass through the wire. If the attackers control the current in a wire, they can control the electromagnetic emission. Attackers can adjust the electromagnetic emission for example to the FM radio band or the GSM, UMTS and LTE frequency bands and use it as an outbound channel.
- Magnetic: By carefully coordinating operations on a computer’s processor cores to create certain frequencies of electrical signals, attackers can electrically generate a pattern of magnetic forces powerful enough to carry a small stream of information to nearby devices even through metal shielding such as Faraday cages. Then the attackers can catch those signals using for example a phone’s magnetometer.
Defending the Air Gap
Being aware of the specific threats and how they work is the first step. Defenders need to be aware that ordinary smartphones can be turned into attack tools. Banning mobiles anywhere near the air gapped systems seems like a prudent policy. Consider also the plethora of вАЬsmart devicesвАЭ that could be compromised and turned into covert channel receivers.
Protecting against the known attack vectors is also a good idea. If USB drives need to be used, then they should be very thoroughly scrutinized first. Auditing of the supply chain is also a good idea. There will always be the possibility of malicious or deceived insiders, so itвАЩs important to log and review actions, looking for suspicious behavior. If questions of staff trust are present and/or extremely high-impact operations are to be conducted, then it is necessary to implement two-person controls, where two individuals must explicitly cooperate to conduct the operation.
Finally, defenders should always remember the assume breach principle. Advanced attackers targeting air gapped systems may have superior capabilities, so it is prudent to expect them to get in one day. Assuming they did get in, how can you design your systems and your response processes? ItвАЩs better to expect the worst rather than deal with an unpleasant surprise.
Do you want to learn more?
We are giving a two-days training about advanced ICS hacking at Ekoparty and HITB Singapore.
Get your ticket!
HITB Singapore: https://conference.hitb.org/hitbsecconf2020sin/sessions/2-day-training-2-advanced-ics-hacking/
Ekoparty Córdoba: https://www.ekoparty.org/ekofederal1/trainings/advanced-ics-hacking
Ekoparty Buenos Aires: https://www.ekoparty.org/eko16/trainings/advanced-ics-hacking-bsas
References and more information:
- https://www.researchgate.net/publication/304916623_Out-of-Band_Covert_Channels-A_Survey
- https://i.blackhat.com/us-18/Wed-August-8/us-18-Guri-AirGap.pdf
- https://www.blackhat.com/docs/eu-17/materials/eu-17-Atch-Exfiltrating-Reconnaissance-Data-From-air gapped-Ics-Scada-Networks.pdf
- https://www.rsaconference.com/industry-topics/presentation/mind-the-air gap-exfiltrating-ics-data-via-am-radios-and-hacked-plc-code
- https://www.nexor.com/resources/white-papers/air gaps-firewalls-and-data-diodes-industrial-control-systems/
- https://www.f5.com/labs/articles/cisotociso/attacking-air gap-segregated-computers
- https://energycentral.com/c/iu/beating-air gap-how-attackers-can-gain-access-supposedly-isolated-systems
- https://journal.cecyf.fr/ojs/index.php/cybin/article/view/4/6
- https://www.sans.org/cyber-security-summit/archives/file/summit-archive-1521579160.pdf
- https://www.tripwire.com/state-of-security/ics-security/air gap-industrial-control-networks/
- https://www.automationworld.com/home/video/13309506/unicorns-air-gaps-do-they-really-exist
- https://www.securityweek.com/air gap-or-not-why-icsscada-networks-are-risk



