On October 10th 2022 Fortinet patched a critical authentication bypass vulnerability affecting three of their products: FortiOS, FortiProxy, and FortiSwitchManager. The vulnerability, identified as CVE-2022-40684 with a CVSS score of 9.6, allows an attacker to login into the affected system with admin privileges, by adding a new SSH key to the admin user.
FortiOS exposes a management web portal that allows users to configure the system. Additionally, users can SSH into the system which exposes a locked-down CLI interface. Horizon3 researchers analysed the differences between Fortinet's vulnerable firmware and it's patched firmware, discovering that the problem was in one function which, if called with specific headers values, could allow to bypass authentication.

Image 1: Vulnerable Function (Source: Horizon3 - https://u6z4d6v3.rocketcdn.me/wp-content/uploads/2022/10/Screen-Shot-2022-10-10-at-11.38.59-AM.png.webp).
This function checks that the client_ip is “127.0.01” and that the User-Agent header matches the second parameter, and gets called with two possible values for the second parameter: “Node.js” and “Report Runner”. The “Node.js” path seems to perform some additional validation, but using “Report Runner” allow to bypass authentication and perform API requests.
Here is an overview of the necessary conditions of a request for exploiting this vulnerability:
Using the Forwarded header the
client_ipshould be set to “127.0.0.1”The
User-Agentshould be set to “Report Runner”
On October 13th a PoC of the vulnerability written in python, by Horizon3 researchers, was published. After a few hours, other PoCs and templates for the vulnerability were published on Github.
Indicators of Compromise (IOCs)
The following indicators of compromise in the device's logs should be checked immediately, according to Fortinet, which is aware of widespread exploitation of this vulnerability:
- user=”Local_Process_Access”
- user_interface=” Node.js”
- user_interface=” Report Runner”
Any HTTP requests to a system's management interface that match the aforementioned criteria should be regarded with suspicion. This vulnerability enables an attacker to change network settings, add new users, and start packet captures on the vulnerable system, among other things. It should be noted that there are other possible conditions that could also be used to exploit this vulnerability. The User-Agent "Node.js" is used, for example, in a modified exploit version. This vulnerability appears to continue a trend among recently identified enterprise software vulnerabilities where improperly validated or overly trusted HTTP headers are involved.
Affected Products
- FortiOS version 7.2.0 through 7.2.1
- FortiOS version 7.0.0 through 7.0.6
- FortiProxy version 7.2.0
- FortiProxy version 7.0.0 through 7.0.6
- FortiSwitchManager version 7.2.0
- FortiSwitchManager version 7.0.0
Fortinet devices affected in Switzerland
Using our CYOBS radar, we detected 533 Fortinet devices in Switzerland still vulnerable to CVE-2022-40684.
As mentioned, an attacker can use this vulnerability to get administration rights over the vulnerable system and do just about anything they want.
We recommend patching or applying the workarounds advised by Fortinet as soon as possible, on an emergency basis. These products are edge devices, which are high-value and high-focus targets for attackers looking to gain internal network access. We expect attackers to focus on CVE-2022-40684 quickly and for quite some time.

Image 2: Vulnerable Fortinet devices detected in Switzerland by CYOBS
The switzerland zones more affected by this vulnerability are:
- Zurich: 260 vulnerable devices
- Vaud: 48 vulnerable devices
- Bern: 44 vulnerable devices
- Valais: 30 vulnerable devices
- Sankt Gallen: 19 vulnerable devices
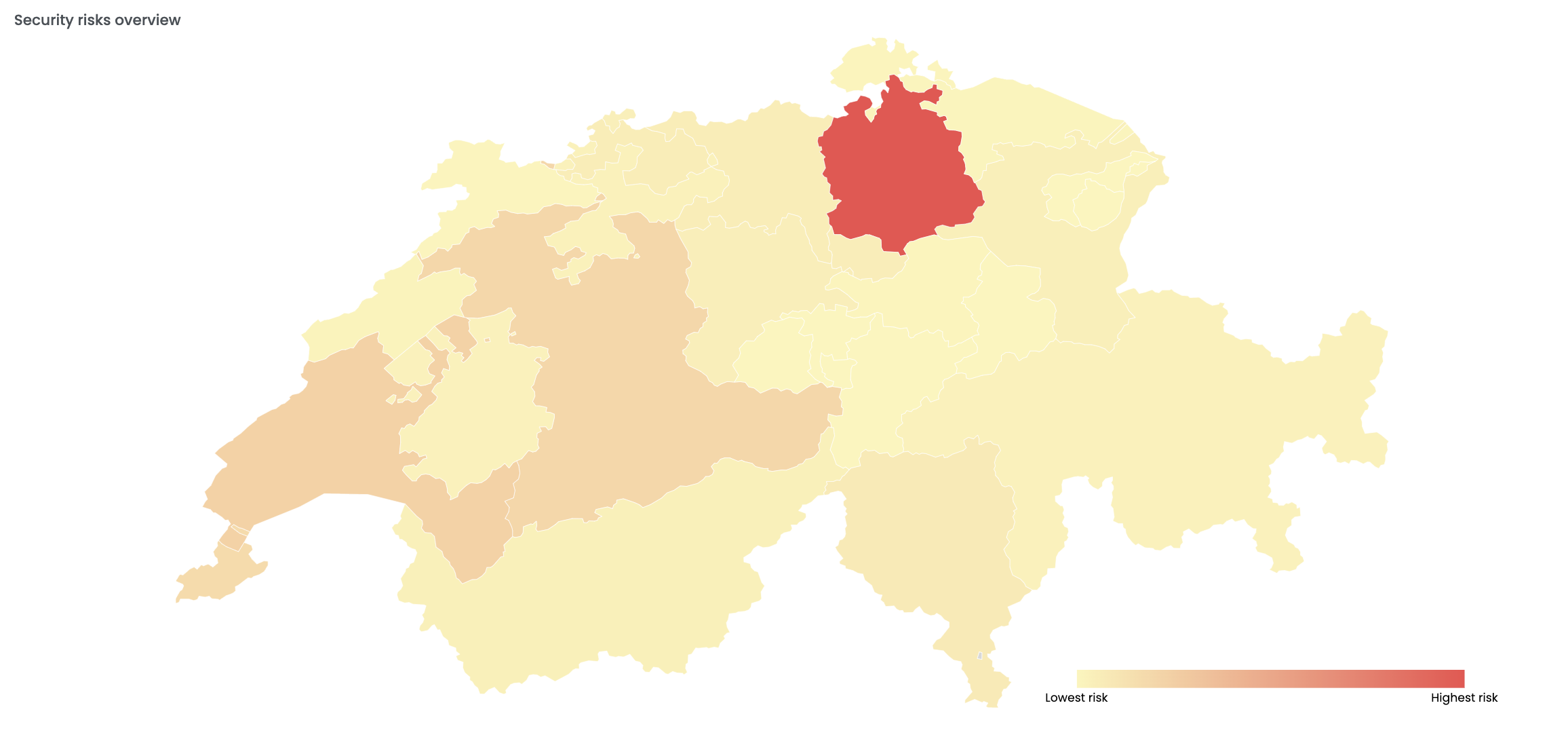
Image 3: Heatmap with Switzerland zones more affected by CVE-2022-40684.
In the following sections, we explain the recommendations published by Fortinet to patch this vulnerability.
Solutions
The ultimate solution to CVE-2022-40684 is applying the software updates provided by Fortinet and upgrade to:
- FortiOS version 7.2.2 or above
- FortiOS version 7.0.7 or above
- FortiProxy version 7.2.1 or above
- FortiProxy version 7.0.7 or above
- FortiSwitchManager version 7.2.1 or above
Workarounds
FortiOS:
The first option is to directly disable the HTTP/HTTPS administrative interface. If you can't do that, the other option is as follows:
1) Limit IP addresses that can reach the administrative interface:
config firewall address
edit "my_allowed_addresses"
set subnet <MY IP> <MY SUBNET>
end
Then create an Address Group:
config firewall addrgrp
edit "MGMT_IPs"
set member "my_allowed_addresses"
end
2) Create the Local in Policy to restrict access only to the predefined group on management interface (here: port1):
config firewall local-in-policy
edit 1
set intf port1
set srcaddr "MGMT_IPs"
set dstaddr "all"
set action accept
set service HTTPS HTTP
set schedule "always"
set status enable
next
edit 2
set intf "any"
set srcaddr "all"
set dstaddr "all"
set action deny
set service HTTPS HTTP
set schedule "always"
set status enable
end
3 )If using non default ports, create appropriate service object for GUI administrative access:
config firewall service custom
edit GUI_HTTPS
set tcp-portrange <admin-sport>
next
edit GUI_HTTP
set tcp-portrange <admin-port>
end
4) Use these objects instead of "HTTPS HTTP "in the local-in policy 1 and 2 below.
FortiProxy:
The first option is to directly disable the HTTP/HTTPS administrative interface. If you can't do that, the other option is as follows:
1) For FortiProxy 7.0.6 only, limit IP addresses that can reach the administrative interface (here: port1):
config system interface
edit port1
set dedicated-to management
set trust-ip-1 <MY IP> <MY SUBNET>
end
FortiSwitchManager:
The only option in this case is to directly disable the HTTP/HTTPS administrative interface.
For further information:
https://www.fortinet.com/blog/psirt-blogs/update-regarding-cve-2022-40684
_____________
References and useful links:
- https://www.horizon3.ai/fortios-fortiproxy-and-fortiswitchmanager-authentication-bypass-technical-deep-dive-cve-2022-40684/
- https://github.com/horizon3ai/CVE-2022-40684
- https://www.horizon3.ai/fortinet-iocs-cve-2022-40684/
- https://www.fortiguard.com/psirt/FG-IR-22-377
- https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2022-40684
- https://socradar.io/what-do-you-need-to-know-about-fortinet-critical-authentication-bypass-vulnerability-cve-2022-40684/
- https://www.wordfence.com/blog/2022/10/threat-advisory-cve-2022-40684-fortinet-appliance-auth-bypass/
- https://www.rapid7.com/blog/post/2022/10/07/cve-2022-40684-remote-authentication-bypass-vulnerability-in-fortinet-firewalls-web-proxies/

