
This model of PLC (like most) has an embedded web service running by default on port 80. Immediately after accessing the web application, we are able to see the validation form which seems to work perfectly, except for a few interesting details...
In most cases (every single time in my particular case), the credentials will be by default those of the manual: 'USER:USER'
When we look at the form, the 'username' is already written. This is a serious issue as the potential attacker's job is already half-done.
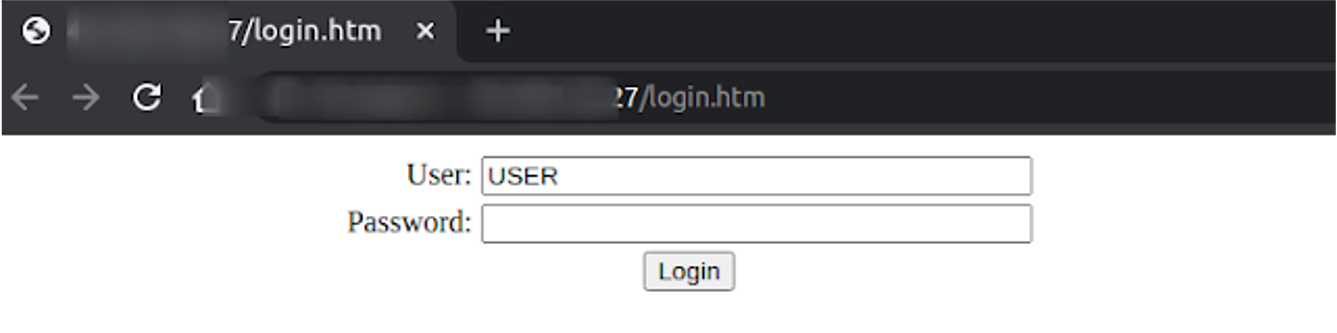
But let's say we come across one of these devices with a changed password. :
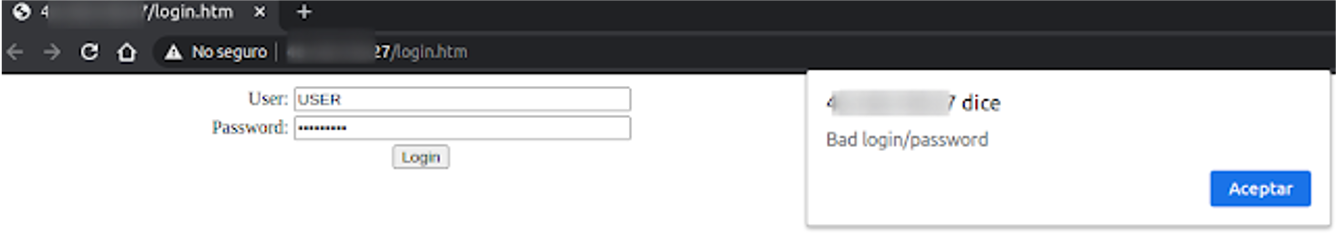
The mechanism that an attacker uses to avoid this security system is as simple as changing the path of the url.
For the PLC 241 model, they can just go from '/login.htm' to '/index2.htm', and in the case of the M251 model the change would be to "/index251.htm"
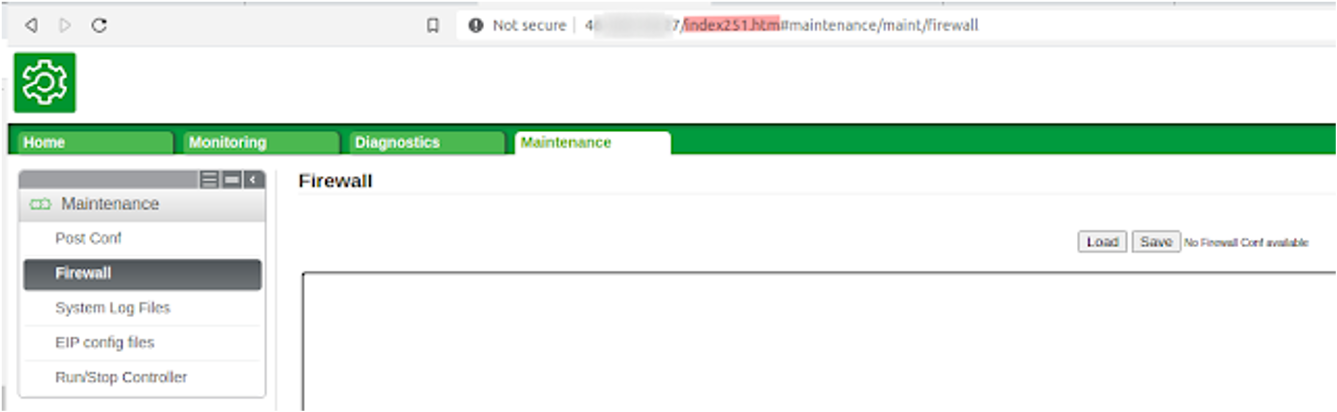
It is worth mentioning that the aforementioned "bypass" does not by default enable all of the device's functionalities.
Greetings,
Industrial Army (@_industrialarmy)

![[Schneider] TM241CE24R & TM251MESE: Login Bypass](/media/img/blog/PowerLogic_PM5560/1594279768638.jpg)