In a recent article for SicherheitsForum, the leading Swiss trade journal for security, Mischa Obrecht, Cybersecurity Specialist, and Jacek Jonczy, Head of Cyber Security Audit & Projects, explained the cybersecurity challenges of highly regulated environments. They outlined the importance of identifying risks in a timely manner, and shared various approaches to ensuring that technology (mastering the flood of data), organisation (integrating the techniques into one's own environments and processes) and data protection (sensitive data must be protected appropriately) are addressed to mitigate security risks in an increasingly complex environment.
«To establish a balance of power or, ideally, to reverse the imbalance between attacker and defender, a comprehensive view is required. Several measures can be taken to achieve this: Digital tripwire and deception approaches aim to identify malicious activities with a high probability and thus defuse the problem of false alarms. Such solutions are designed to ensure that there is no reason for any normal user to interact with the tripwire system.»
Another approach is to improve accuracy and speed in detecting and dealing with potential incidents. This can be achieved by sharing structured information about new threats (threat intelligence - see Figure below), automating and orchestrating the response, and correlating and contextualising the physical and cyber dimensions: In addition to classic IT infrastructure, the corresponding physical level as well as other technical levels (e.g., operational technology) must be considered. Affected systems must be put in context with each other and events from different domains must be correctly correlated (cross-domain correlation).”
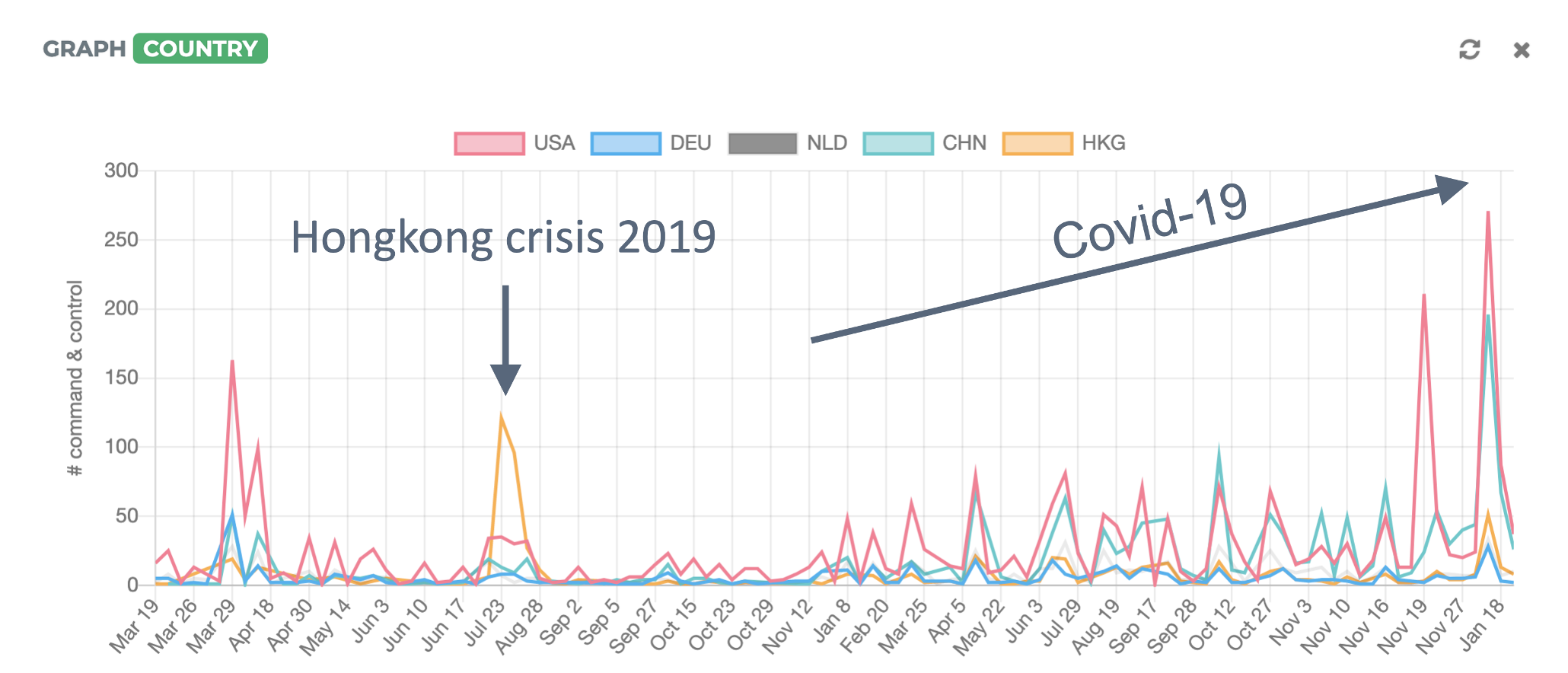
Figure 2: Threat intelligence using the example of https://ratspotting.ch/
RAT stands for "Remote Access Toolkit". It refers to the attackers' infrastructure, which is used to remotely control successfully hacked IT systems (command & control infrastructure). Blocking connections to such infrastructure is an effective means of protecting one's own systems. Here, too, there is a close connection between "real" events and developments in cyberspace. In 2019, for example, RATspotting observed a sharp increase in Command & Control infrastructure in Hong Kong during the politically motivated riots. Since the outbreak of Covid-19, the increasing use of home offices can also be linked to an increase in the use of malicious RATs.
Download the full article (German only).

