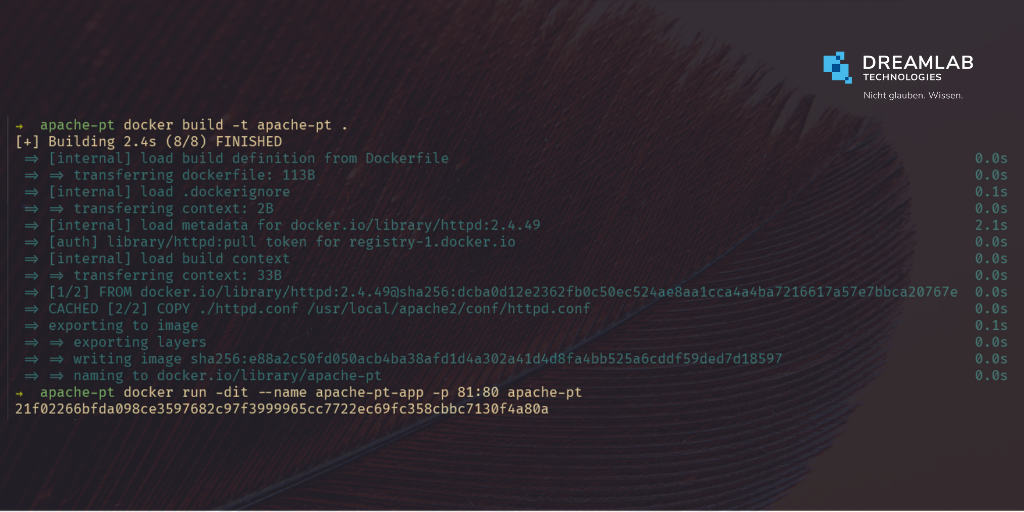
On Tuesday, 5 October 2021, Apache Software Foundation released Apache HTTP 2.4.50 to fix an actively exploited path traversal vulnerability in version 2.4.49 (tracked as CVE-2021-41773). A flaw that allowed threat actors to view the contents of files stored on a vulnerable server.
Soon after the update was released, security researchers analyzed and disclosed working exploits for the vulnerability and discovered that it could¬†be used for remote code execution¬†if the mod_cgi module was loaded and the default “Require all denied” option was missing. With so many servers potentially vulnerable to remote code execution, it became even more critical for admins to update their Apache HTTP servers.
Today, 7 October 2021, Apache released an emergency update fix, version 2.4.51. This new path traversal vector is being tracked as¬†CVE-2021-42013, and it was disclosed by¬†DreamlabвАЩs Cybersecurity Consultant, Juan Escobar, together with Fernando Mu√±oz from NULL Life CTF Team, and Shungo Kumasaka.
It is strongly recommended that admins immediately upgrade their servers to Apache HTTP 2.4.51 to remove any attack vectors left after the previous patch.

