What is banner grabbing?
Banner grabbing is the process of obtaining information about the infrastructure, or technology, behind a service. In particular, through banner grabbing, it is possible to obtain information about the vendor, product and/or version of the software that runs behind a port. It should also be noted that the "How is it done?" will depend on the communication protocol of the service, so this entry will cover how banner grabbing can be performed when the communication protocol is Modbus/TCP.
In summary, from a malicious actors viewpoint, banner grabbing could allow more precise attacks on the target to be prepared, or allow a direct search for known vulnerabilities affecting a particular product and version to be carried out.
Modbus Overview
Modbus is a data communication protocol originally published by Modicon (now Schneider Electric) in 1979 for use with its Programmable Logic Controllers (PLCs). A PLC is a device used in industrial systems to automate electromechanical, electro-pneumatic and electro-hydraulic processes.

Figure 1 PLC Modicon M340
Modbus is one of the most widely used protocols found in ICS or operational technology (OT) environments, since contrary to many of the other industrial protocols, it is an open source protocol. Therefore, it is not only royalty free, but also upon closer inspection relatively easy to understand and deploy, with a specification document that is only 50 pages, including both contents and Annexes.
The TCP/IP port reserved for communicating with the Modbus protocol is 502. Modbus/TCP is a request/reply protocol between a server and a client, meaning a device operating as a client can poll one or more devices operating as a server. This means a server device cannot send information on its own; it must wait to be asked for it by the client. Modbus server devices can be visualized as having an internal spread sheet filled with numbers. The "columns" in a Modbus device's "spread sheet" are more formally known as registers. Register types may be a coil, a discrete input (status input), an input register, or a holding register. The Modbus client will ask a server for its data value or number found in a given row and column, and the server will respond by sending that piece of data back to the client. The Modbus client can also ask to write or tell the server device what value to place into its data table at a given row and column.
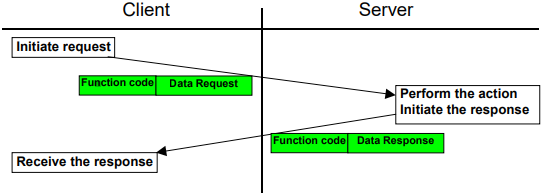
Figure 2 client - request diagram
The commonest form of Modbus protocol is RTU over RS-485. Modbus RTU is a relatively simple serial protocol that can be transmitted via traditional UART technology. The discussion here will focus on Modbus TCP that encapsulates Modbus RTU request and response data packets in a TCP packet transmitted over standard Ethernet networks. Modbus function codes are elements of this Modbus request/reply protocol data unit (PDU). The following image shows the structure of a Modbus/TCP package.
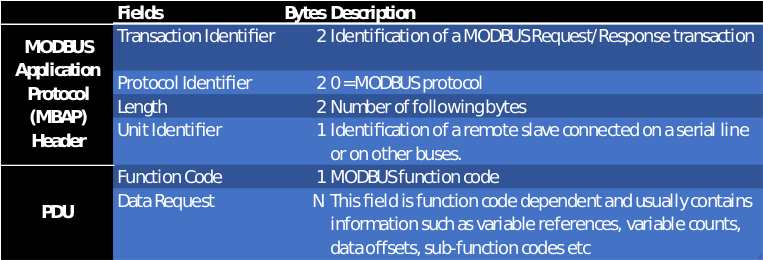
Figure 2 Modbus package
Modbus Functions codes
There are three categories of Modbus Function codes: Public Function Codes, User-Defined Function Codes and Reserved Function Codes. Specifically, 1-65, 72-100 and 110-127 are Public Function Codes that are well defined in the documentation, validated by the MODBUS.org community and guaranteed to be unique. Function codes from 65 to 72 and between 100 and 110 are User-Defined ones, meaning an user can select and implement a function code that is not supported by the specification (not a public function one), but it means that there is no guarantee that the use of the selected function code will be unique, which could cause issues with interoperability and functionality, especially in more complex deployments. The Reserved Function Codes are 9, 10, 13, 14, 41, 42, 90, 91, 124, 126, 127. These are all part of the public function code ranges, but as they are currently used by some companies for legacy products, they are not truly available for public use.
In industrial environments, the public function codes most frequently interacted with, are Modbus functions that allow data to be read and written from or to the server device, such as '01 (0x01) Read Coils', '03 (0x03) Read Holding Registers', '05 (0x05) Write Single Coil', '06 (0x06) Write Single Register' or '16 (0x10) Write Multiple registers'. 
Figure 3 Public Function Code Definition
Function Code 43/14 (Read Device Identification)
Function code 43/14 allows the identification and additional information related to the physical and functional description of the PLC to be read. This data is represented as a set of objects with their respective identifier. These objects can be classified into three categories:
Basic Device Identification
Regular Device Identification
Extended Device IdentificationBanner Grabbing
Additionally, all objects in the Basic category are mandatory: vendor name, product code and revision number. This contrasts with the Regular and Extended categories, which are optional. The following table shows the details of each object:
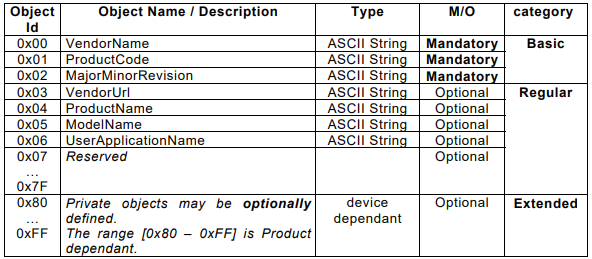
Figure 4 detail objects Fn 43/14

Figure 5 Fn 43/14 (0x2B/0x0E) Read Device Identification
The following example illustrates a Read Device Identification request for a «Basic Device Identification» object:
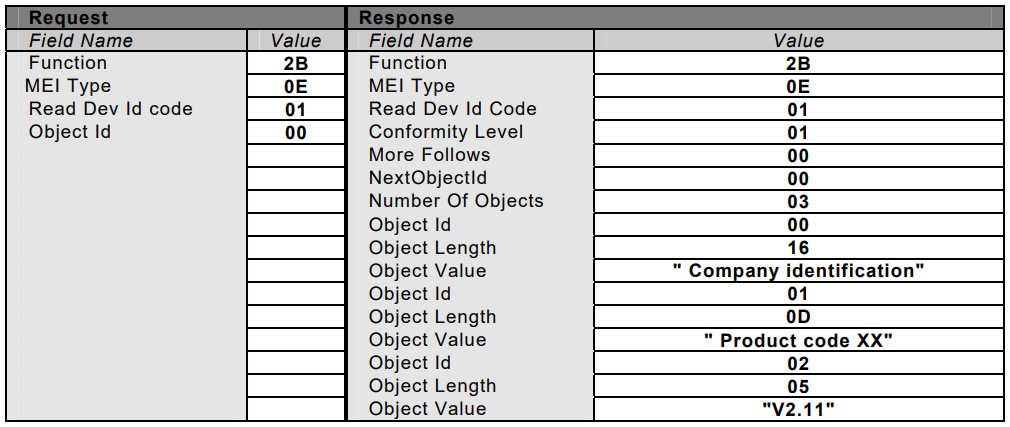 Figure 6 Example of a Read Device Identification request
Figure 6 Example of a Read Device Identification request
With this information, it is possible to program a Python client that sends a Read Device Identification request to the PLC and prints the response on the console:

Figure 7 source code Modbus_tcp.py
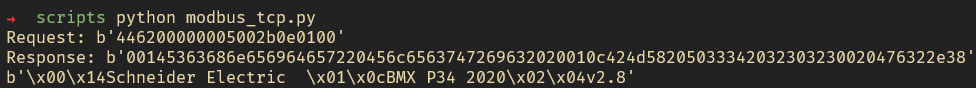
Figure 8 script execution Modbus_tcp.py
By executing this script, the following information about the PLC device is obtained:
Vendor Name: Schneider Electric
Product Code: BMX P34 2020
Revision: v2.8
Finally, the content of this request can be seen in greater detail with a Wireshark traffic capture.


Tool
Based on the theory presented above, Dreamlab Chile I+D team developed a tool to perform banner grabbing for the Modbus/TCP protocol using the 43/14 function code. This tool can be downloaded from our repository at GitHub:
Quick Start
Banner Grabbing
git clone https://github.com/industrialarmy/hello_proto
cd hello_proto/Modbus
python3 banner_grabbing.py <Modbus host>
Example
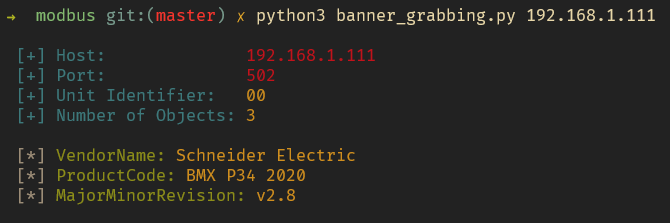
Figure 9 execution of tool banner_grabbing.py
Metasploit Module
In addition, the team have developed an Metasploit auxiliary scanner module for this tool
Quick Start
use auxiliary/scanner/scada/Modbus_banner_grabbing
set RHOST <IP>
run
Example
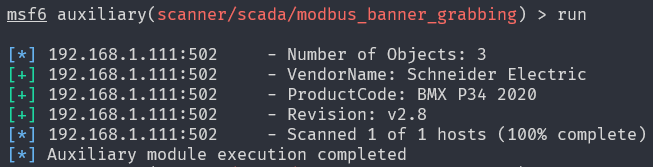 Figure 9 execution of auxiliary module «Modbus_banner_grabbing»
Figure 9 execution of auxiliary module «Modbus_banner_grabbing»
Do you want to learn more?
We are giving a two-days online training about Attacking and Securing Industrial Control Systems at Blackhat USA on August 2nd to 3rd 2021 and HITB on August 24th to 25th 2021.
Get your ticket!
- BlackHat USA (US Pacific Timezone): https://www.blackhat.com/us-21/training/schedule/index.html#attacking-and-securing-industrial-control-systems-ics-21885
- HITB (CEST Timezone): https://sectrain.hitb.org/courses/attacking-and-securing-industrial-control-systems-ics-hitb2021sin/
References
Juan Escobar
Cybersecurity Consultant at Dreamlab Technologies
Sarka Pekarova
Security Consultant at Dreamlab Technologies
Check out also our trainings schedule for more dates: https://dreamlab.net/en/education/trainings-schedule/.

