
Downloading the firmware
The device's firmware has been downloaded and decompiled.
Source: https://support.industry.siemens.com/cs/document/62567396/ozw672-factory-firmware-update-and-system-definition?dti=0&lc=en-WW

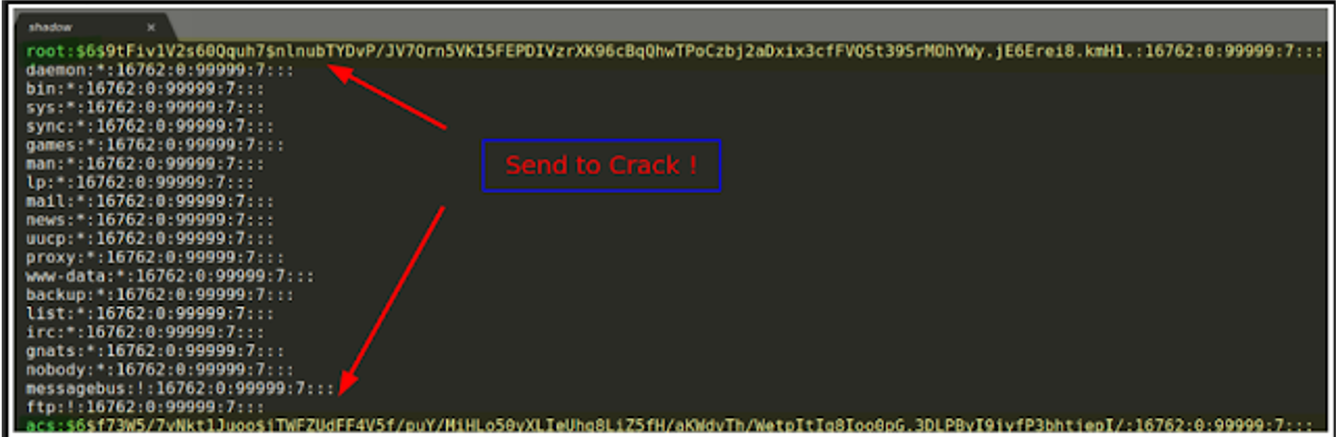
Readings of key resources are performed. Such as: "/etc/shadow"

Immediately, credentials are sent for cracking:
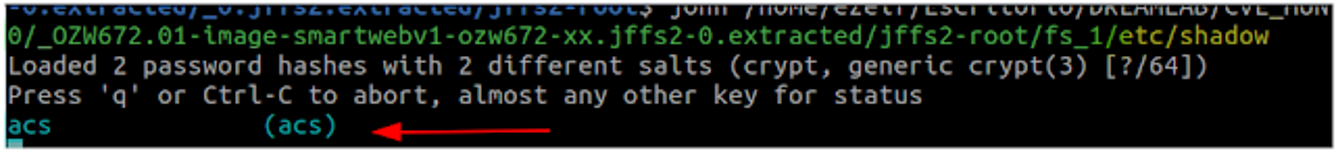
It was only possible to break the hash that corresponds to the user "ACS"

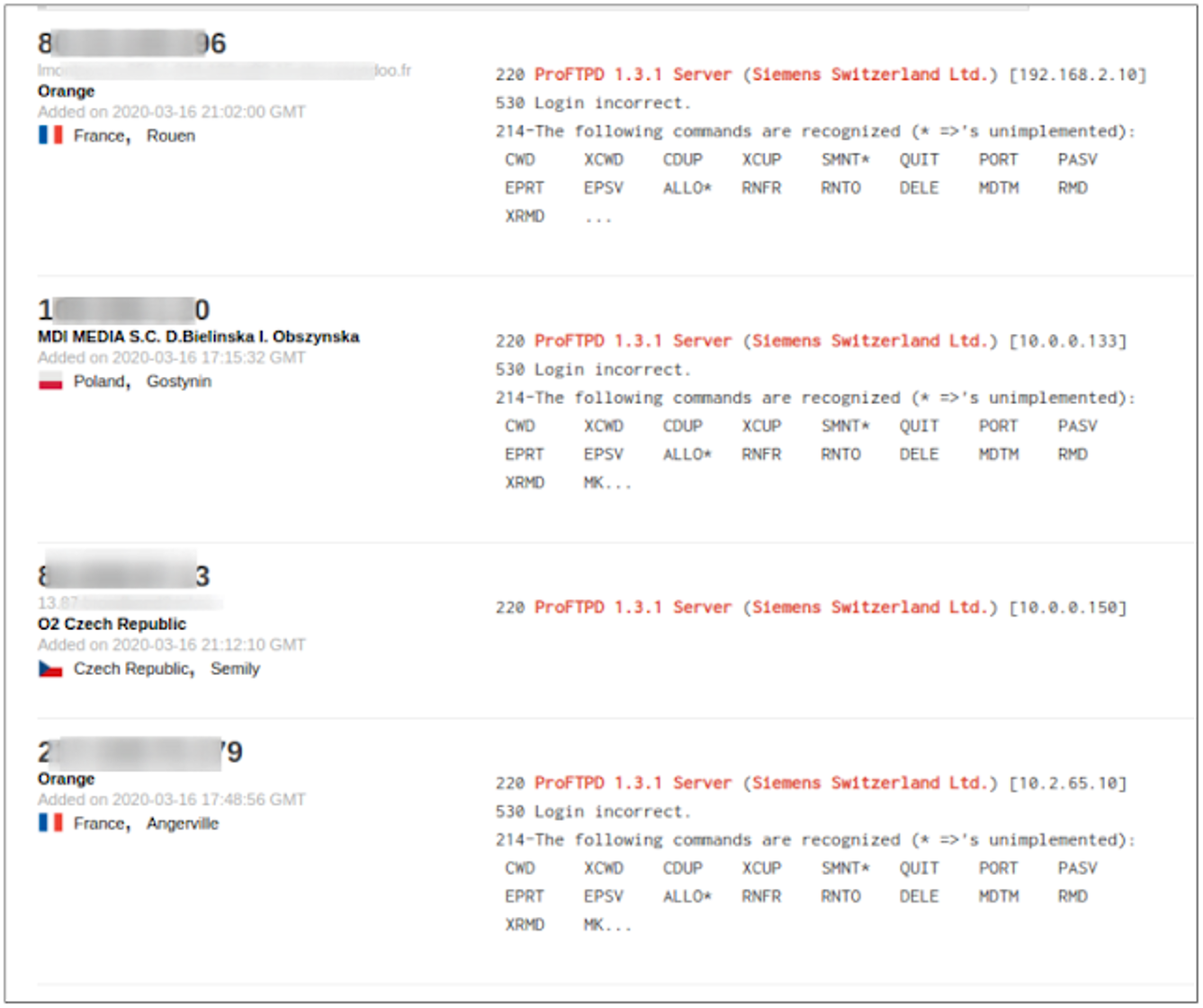
Exposure
The "Shodan" platform (https://shodan.io) is then used to provide a representative sample of the degree of exposure of the device under analysis.
The search criteria used (Dork) was: "ProFTPD 1.3.1 Server (Siemens Switzerland Ltd.)"

Validation
We then validate by crosschecking the credentials with the results obtained. As shown in the screenshot below, the credentials are valid.

Report: This vulnerability was duly reported to Siemens. However, the problem was already known. A CVE was assigned to it: CVE-2017-6872.
ANNEXES
Device manual: https://www.downloads.siemens.com/download-center/Download.aspx?pos=download&fct=getasset&id1=A6V10744843
https://cert-portal.siemens.com/productcert/pdf/ssa-563539.pdf https://www.us-cert.gov/ics/advisories/ICSA-17-187-01

![[Siemens] OZW672: Undocumented user ("Back door"), with weak password (CVE-2017-6872)](/media/img/blog/_Siemens__OZW672/Picture11.png)