By Yamila Levalle, Security Researcher at Dreamlab Technologies
Tactics and Techniques Used in Known ICS Attacks
The evidence that ICS systems are a prime target for sophisticated attackers, is clearly shown by the marked increase of attacks aimed at ICS facilities. Havex, Industroyer and Triton use advanced techniques to obtain information, hijack controls, cause disruption and shut down critical systems. We will analyse the three aforementioned attacks and map their tactics and techniques to the ATT&CK for ICS Matrix.
Triton or Trisis
Triton malware was originally discovered targeting a Saudi Arabian petrochemical plant in 2017, and targeted a vulnerability in Triconex safety controllers (SIS), meaning that if successful, the attack could have caused the release of poisonous gasses or deadly explosions. The particular features of this industrial malware are:
- Initially gains access to the system by gaining remote access to a SIS engineering workstation.
- Masquerades as trilog.exe, the Triconex software for analyzing SIS logs.
- Detects Triconex controllers on the network by sending certain UDP broadcast packets over port 1502.
- Exploits a Triconex firmware vulnerability to disable a firmware RAM/ROM consistency check and inject a payload, imain.bin, into the firmware memory.
- Reprograms SIS logic to allow unsafe conditions to persist.
- Manipulations of controls result in dangerous malfunctions.
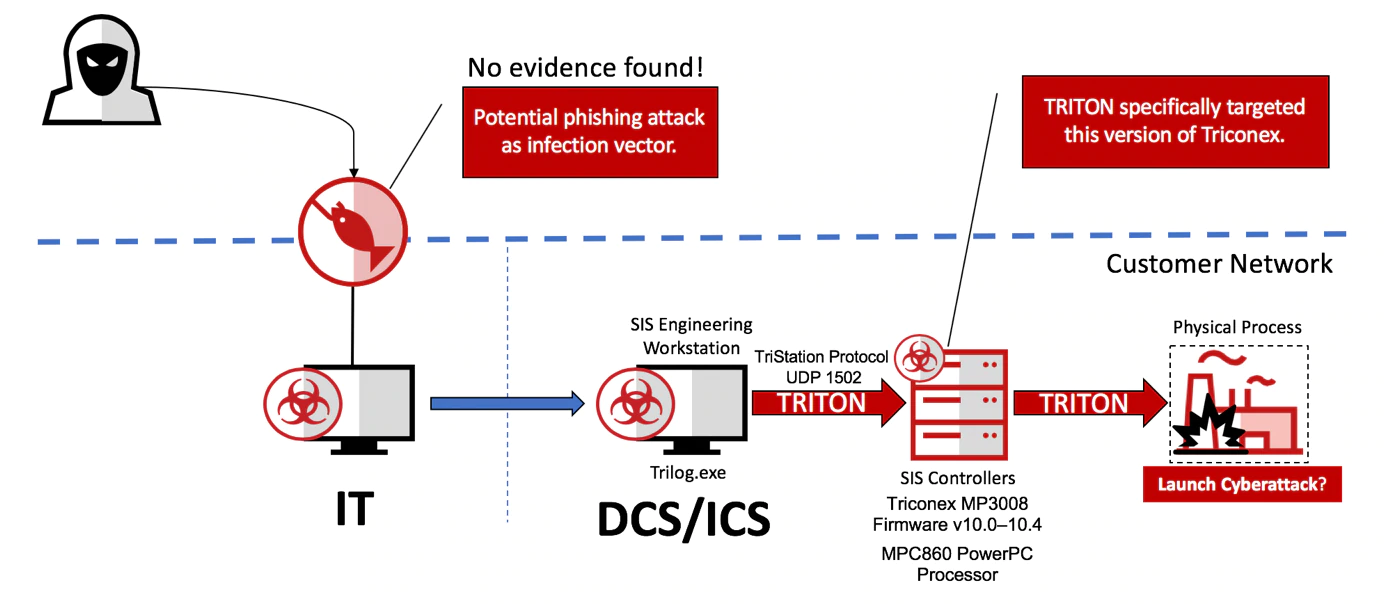
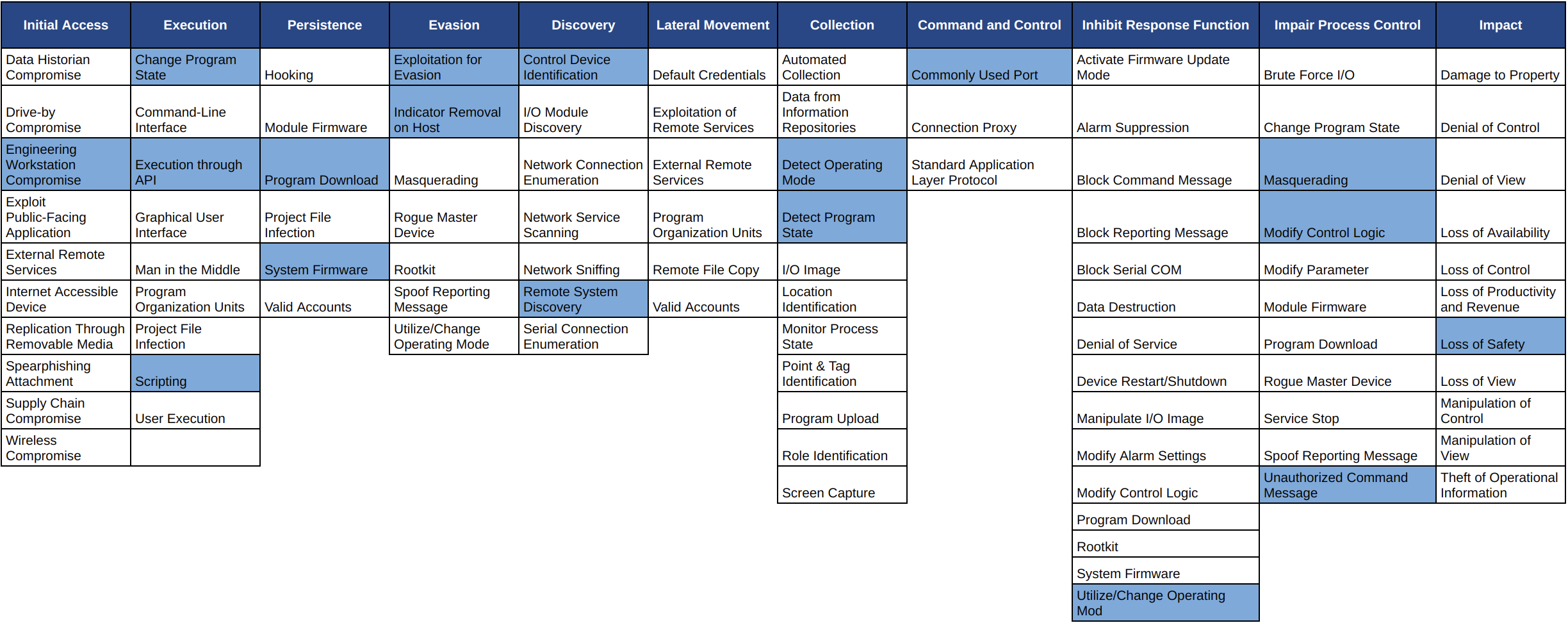
So, how does the Triton attack break down into the MITRE ATT&CK for ICS tactics and techniques? The coloured cells in the matrix below highlight the techniques used in Triton-based attacks:
Industroyer or Crashoverride
Industroyer, is a sophisticated multi-component malware designed to disrupt the working processes of electrical substations using IEC101, IEC104, IEC61850 and OPC protocols. The particular features of this industrial malware are:
- Sends commands directly to the RTU using industrial protocols, including the opening and closing of breakers (substations switches) quickly and continuously.
- Blocks serial ports, preventing communications between legitimate devices and affected devices.
- Carries out a network discovery through the OPC protocol and a port scanner.
- Exploit a vulnerability of Siemens SIPROTEC relays, which can lead to a denial of service.
- Includes a wipe module that deletes data and any other file that could lead to its tracking and renders systems useless. A backup copy is required to put it back into operation.
- The successful use of this malware, as it was the case of power plants in Ukraine, can cause blackouts.
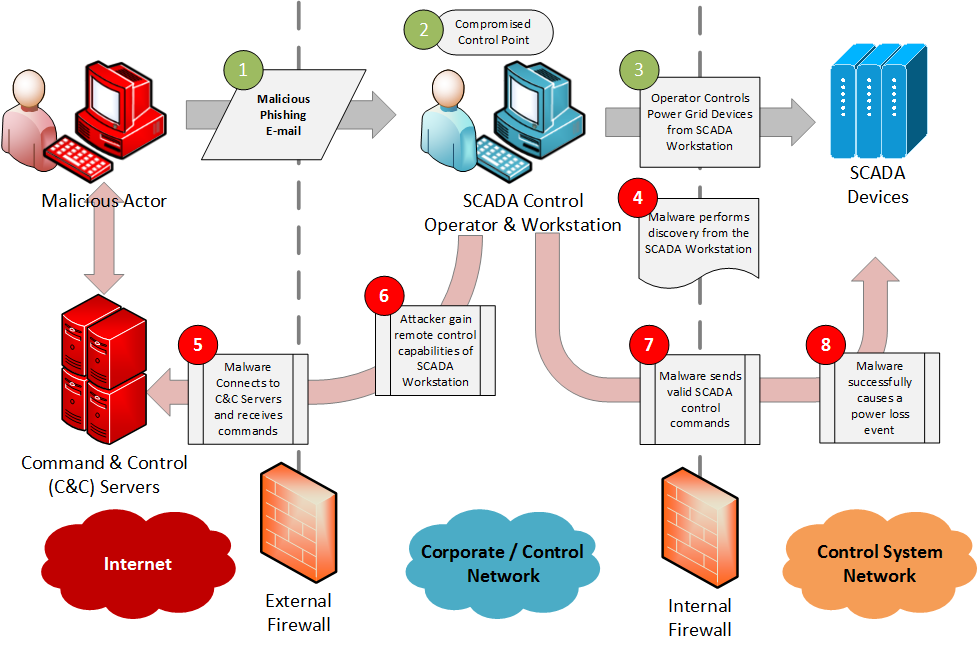
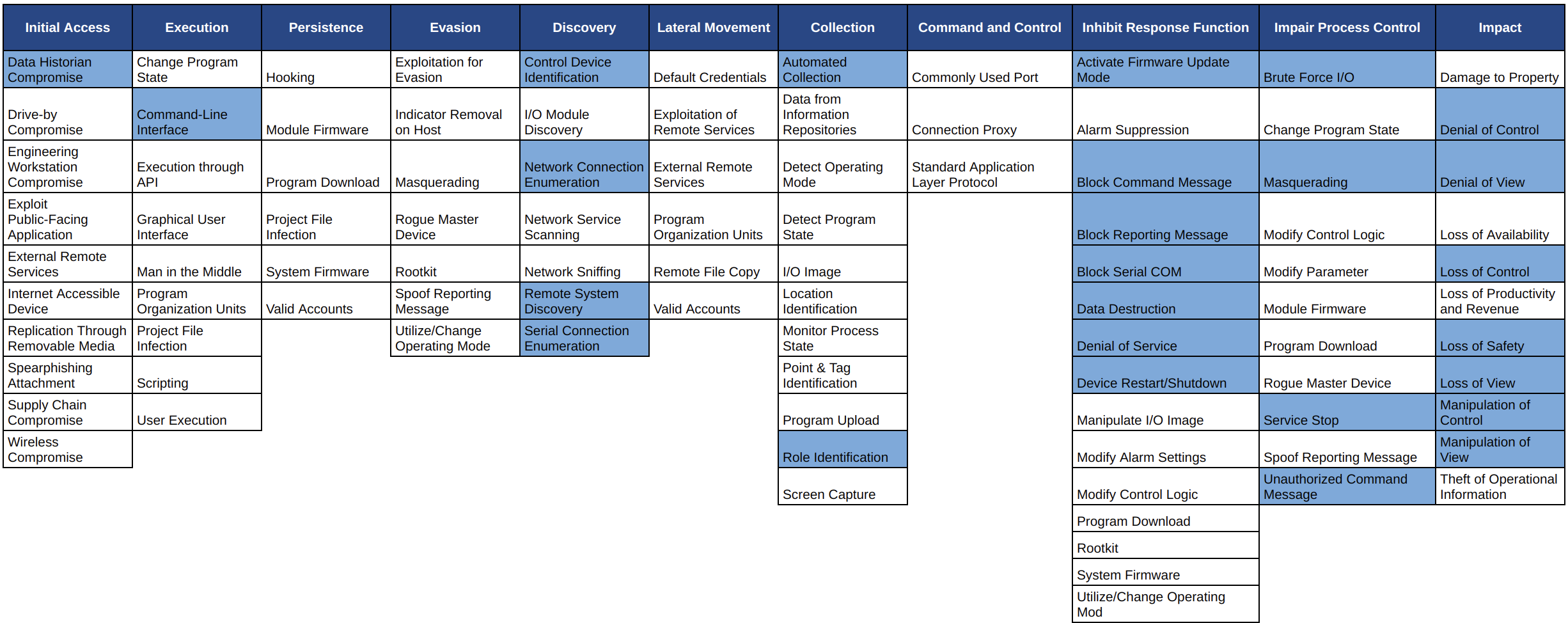
So, how does the Industroyer attack break down into the MITRE ATT&CK for ICS tactics and techniques? The coloured cells in the matrix below highlight the techniques used in Industroyer-based attacks:
Dragonfly / Havex
The Dragonfly cyber-espionage effort is an ICS focused malware campaign that uses multiple vectors for infection. These include:
- Email spear phishing campaign, sending emails containing a malicious PDF attachment to selected executives and senior employees in target companies
- Redirects from energy related websites to compromised legitimate websites hosting the Lightsout exploit kit
- Trojanized update installers on at least 3 industrial control systems (ICS) vendor websites, in what are referred to as watering hole-style attacks. The software installers for these vendors were infected with malware known as the Havex Trojan.
These techniques could have allowed attackers to access the networks of systems that have installed the trojanized software. In particular, the payload gathers OPC server information and also has the capability of enumerating OPC tags. The Havex payload has caused multiple common OPC platforms to intermittently crash, this could cause a denial of service effect on applications reliant on OPC communications.
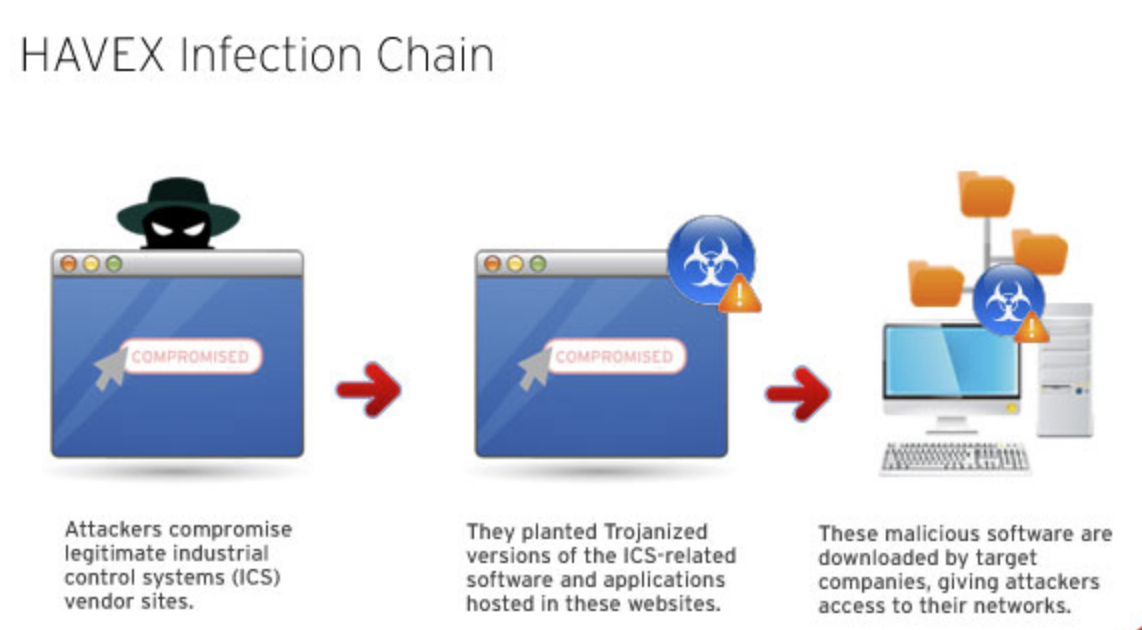
So, how does the Dragonfly attack break down into the MITRE ATT&CK for ICS tactics and techniques? The coloured cells in the matrix below highlight the techniques used in Dragonfly-based attacks:

ATT&CK for ICS Use Cases
One of the interesting aspects about applying the ATT&CK structure and methodology to a new technology domain is that many of the existing use cases are transferable. Some of the use cases considered in ATT&CK for ICS include:
вАҐ Adversary Emulation
вАҐ Behavioural Analytics
вАҐ Cyber Threat Intelligence Enrichment
вАҐ Defensive Gap Assessment
вАҐ Red Teaming
вАҐ SOC Maturity Assessment
вАҐ Failure Scenario Development
вАҐ Cross-Domain Adversary Tracking
вАҐ Educational Resource
The Failure Scenario Development¬†use case involves identifying failures that are known to affect a system. The next step involves understanding whether the failure is cyber inducible. Since physical attacks are not within the scope of ATT&CK for ICS, there is a requirement that these failures have a cause that is traceable back to cyber. Once cyber inducible failures are identified, a sequence of ATT&CK techniques that could potentially lead up to this failure can be identified. These actions represent some of the initial work an adversary or red team would go through when targeting a control system. This can provide defenders with valuable information to better understand where to invest in defences to disrupt an adversaryвАЩs path to inducing critical failures.
ATT&CK for ICS can also act as a critical resource in conjunction with other ATT&CK knowledge bases to enable the Cross-Domain Adversary Tracking use case. Adversaries rely on and exploit many platforms to negatively impact control systems. To gain the best understanding of adversaries who target control systems, it is important to track their behaviour as it applies to the technology domain(s) that they target and/or utilize. If adversary actions associated with one technology domain are solely considered, key parts of the big picture will invariably be missed. Therefore, adversary behaviour associated with multiple technology domains may need to be taken into account. The most obvious ATT&CK knowledge bases to inform Cross-Domain Adversary Tracking in ICS environments are the Enterprise and ICS knowledge bases. Utilizing these two knowledge bases together can allow you to track the behaviour of adversaries as they move through IT to impact control systems. It can also highlight key system interfaces that are commonly abused.
Use cases such as Behavioural Analytics, Defensive Gap Assessment, and SOC Maturity Assessment are closely coupled with the ability to detect techniques. The initial release of ATT&CK for ICS does not include a Detection section within each technique and has instead focused on mitigations. The addition of detections is planned for future versions of ATT&CK for ICS.
Conclusions
MITRE ATT&CK for ICS Matrix not only documents all the different tactics and techniques of the adversaries in a knowledge base, but also presents them as they appear in the real world: as pieces of a complete story, rather than isolated actions. That’s how the most value can be gained from using the MITRE ICS framework: by looking at these techniques as a whole, and understanding how they work within the complete story of an attack. Organisations should aim to achieve an holistic coverage across the matrix, and this goes beyond being able to check the boxes of individual techniques. It means having the ability to detect risky abnormalities, manage vulnerabilities, achieve visibility of the devices and how they behave across the entire ICS network and¬†understand where to invest in defences to disrupt an adversaryвАЩs path to cause critical failures.
Do you want to learn more?
We are giving a two-days training about Advanced ICS hacking at Ekoparty and HITB.
Get your ticket!
- HITB (Online РEnglish РSingapore Timezone): https://conference.hitb.org/hitbsecconf2020sin/sessions/2-day-training-2-advanced-ics-hacking/
- Ekoparty (Online РSpanish): https://www.ekoparty.org/eko16/trainings/advanced-ics-hacking-bsas
________________
References and Related Content:
- https://collaborate.mitre.org/attackics/index.php/Software
- https://medium.com/mitre-attack/launching-attack-for-ics-2be4d2fb9b8
- https://scadahacker.com/files/havex/Symantec%20-%20Security%20Response%20-%20Dragonfly%20v1.0.pdf
- https://ics.kaspersky.com/media/ics-conference-2019/12-Marina-Krotofil-If-I-Were-MITRE-ATTCK-Developer-Challenges-to-Consider-when-Developing-ICS-ATTCK-Attacker-perspective.pdf
- https://www.us-cert.gov/ics/alerts/ICS-ALERT-14-176-02A
- https://www.nozominetworks.com///downloads/US/Nozomi-Networks-TRITON-The-First-SIS-Cyberattack.pdf
- https://archive.f-secure.com/weblog/archives/00002718.html
- https://www.sans.org/reading-room/whitepapers/ICS/impact-dragonfly-malware-industrial-control-systems-36672


