By Yamila Levalle, Security Researcher at Dreamlab Technologies
MITRE introduced the Adversarial Tactics, Techniques, and Common Knowledge (ATT&CK) in 2013 as a central knowledge base for adversary behaviour. It is based on real observations of cyber security incidents and maps the tactics, techniques and procedures (TTPs) to its knowledge base. The framework categorizes its information in tactics, techniques, mitigations, groups and software.
Tactics can be seen as the phases of an attack, each phase has a certain goal which the adversary tries to reach. Each tactic has certain techniques that represent how to achieve these goals. For every technique there are mitigations detailing how to protect the organisation. Adversaries use different types of software which are also represented in the framework. All of this information can be linked to groups, that are sets of related intrusion activity tracked by a common name in the security community, also sometimes referred to as campaigns.
The greatest strength of the ATT&CK framework is its focus on threat behaviours rather than indicators. Why is this important? While it is trivial for an Activity Group to change IP addresses, domain names, file hash values and network artefacts, it is extremely difficult  to change the tactics, techniques and procedures (TTPs) or behaviours behind attacks. Changing TTPs requires investment in new technology and resources, which is considerably more expensive and time-consuming than something as simple as acquiring a new domain name. By focusing on threat behaviours, defenders are able to create detections with a high confidence rating and increased longevity.
Until the beginning of this year the ATT&CK matrices did not focus on the ICS world.
Why ATT&CK for Industrial Control Systems – ICS?
The last several years have seen an increase in the awareness of threats to operational technology (OT) environments, however it is one thing to be aware of the vulnerabilities of ICS networks and another to actually protect ICS networks against those threats. ICS networks are comprised of unmanaged, often-unpatched devices, that cannot be protected using the same security strategies as the traditional IT environment. Because of the unique nature of these devices, the methods that attackers use to compromise them are often very different from the more well-known methods used to compromise IT systems. This means that ICS networks security cannot simply fall under the jurisdiction of IT security. They provide two completely different challenges, that require significantly different approaches.
ATT&CK for ICS was created out of a need to better understand, concentrate, and disseminate knowledge about adversary behaviour in the ICS technology domain. There are several motivations to introduce a separate ATT&CK matrix for ICS:
- First, adversaries pursue different goals in the ICS domain. The three generally accepted objectives of information security are represented by the Confidentiality, Integrity and Availability (CIA) triad, prioritizing confidentiality ahead of the other two objectives. In ICS security, the priority is on the industrial process, as the whole ICS environment has been built specifically to keep the industrial process alive and running efficiently. This means that availability and integrity become the priority, altering the intended goals of the attackers.
- The second reason is that the ICS domain differs in technology. The devices are often embedded platforms using specialized process automation protocols and hosting a wide variety of frequently custom ICS applications.
- Finally, an attack on the ICS domain has specific consequences. On top of possible process and operation unavailability, control over processes could be lost, leading to major and potentially even life threatening safety concerns.
ATT&CK for ICS Matrix
ATT&CK for ICS includes the ATT&CK for Enterprise techniques that can be leveraged by an adversary in the final stages of either a targeted or un-targeted attack against an industrial process. Whilst there is significant overlap between the Enterprise and ICS technology domains, ATT&CK for ICS has a primary focus on the actions that adversaries take against the non-IT based systems and functions of ICS. Its aim is to capture and define distinctions in ICS environments, from tactics and techniques, to domain specific assets and technology. Even within ICS, industry verticals (Electric, Oil and Gas, Manufacturing) have unique characteristics. ATT&CK for ICS is vertical agnostic and will work equally for ICS systems that support a wide range of industrial processes. ICS networks are highly heterogeneous environments, the ICS specific assets serve a consistent function regardless of the underlying operating system, hardware platform or application.
In the following image you can view the functional levels of the Purdue Model that are the focus of ATT&CK for ICS:
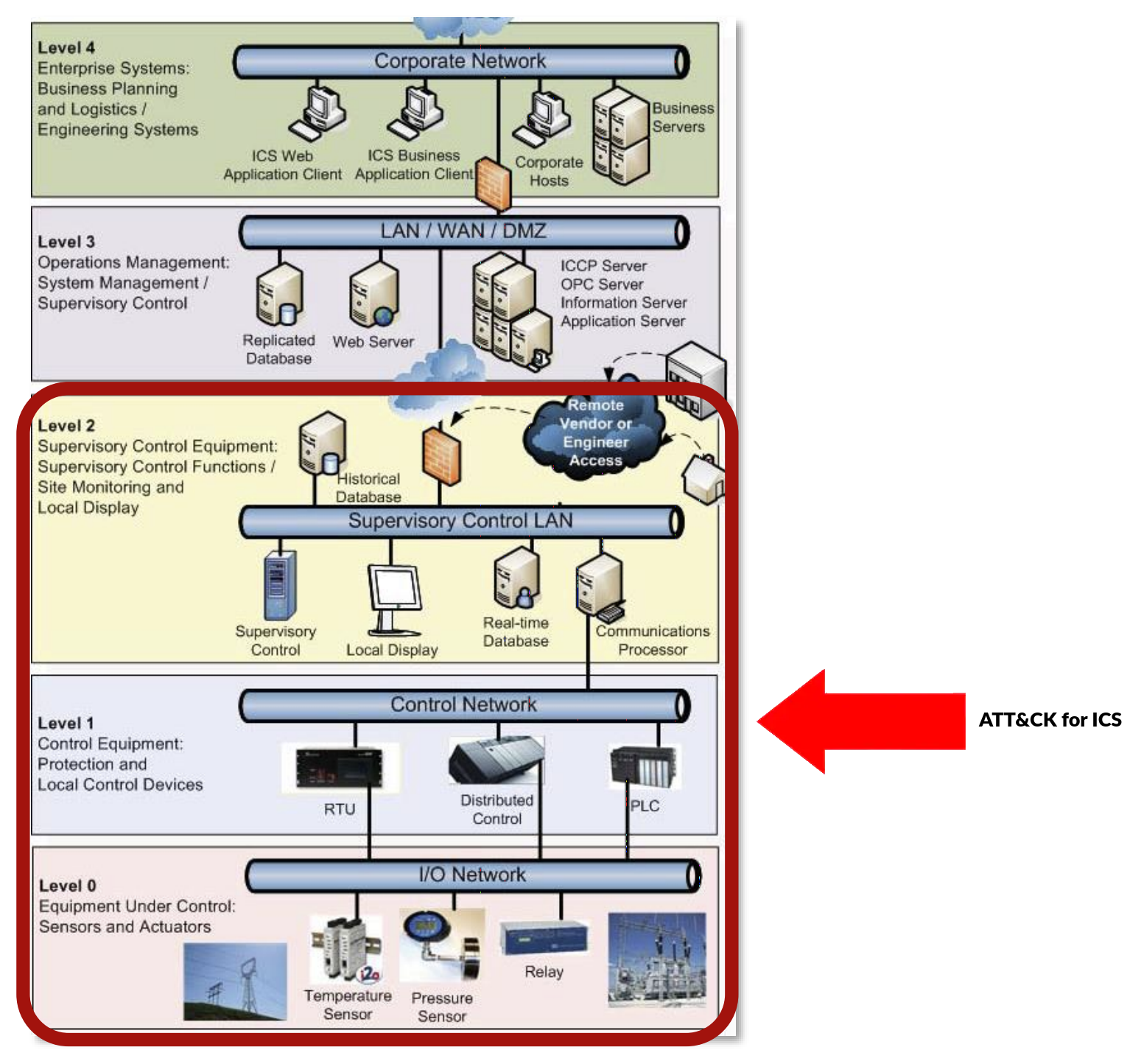
MITRE introduced the ATT&CK for ICS matrix on 7th January 2020, where new tactics, techniques, software and groups relevant to ICS are presented: https://collaborate.mitre.org/attackics/index.php/Technique_Matrix.
This matrix consists of eleven tactics that threat actors could use to attack an ICS environment, these are then broken down into 81 specific techniques. Ultimately, this database describes every stage of an ICS attack from initial compromise to ultimate impact:
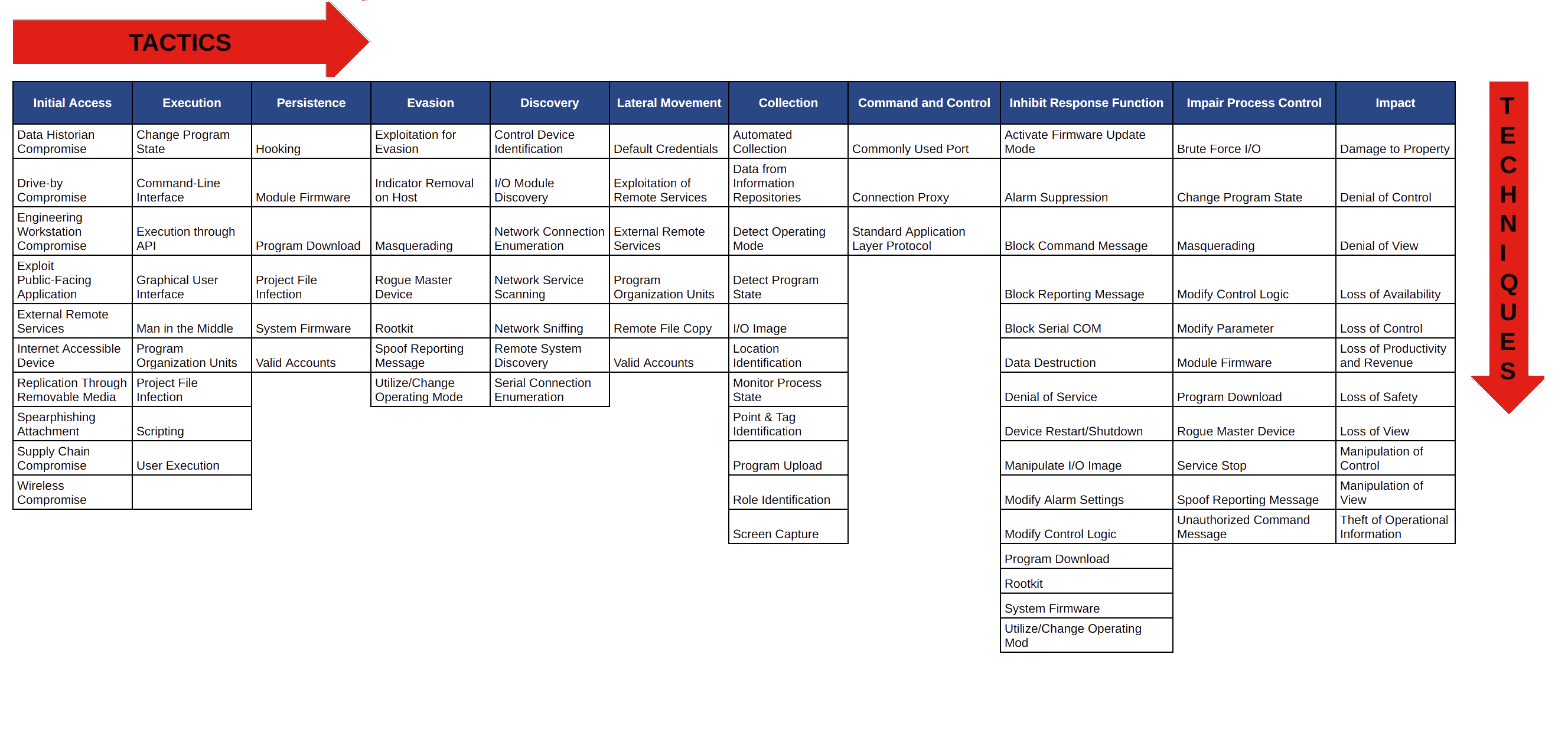
Below is the list of all 11 tactics in ATT&CK for ICS and their corresponding description:
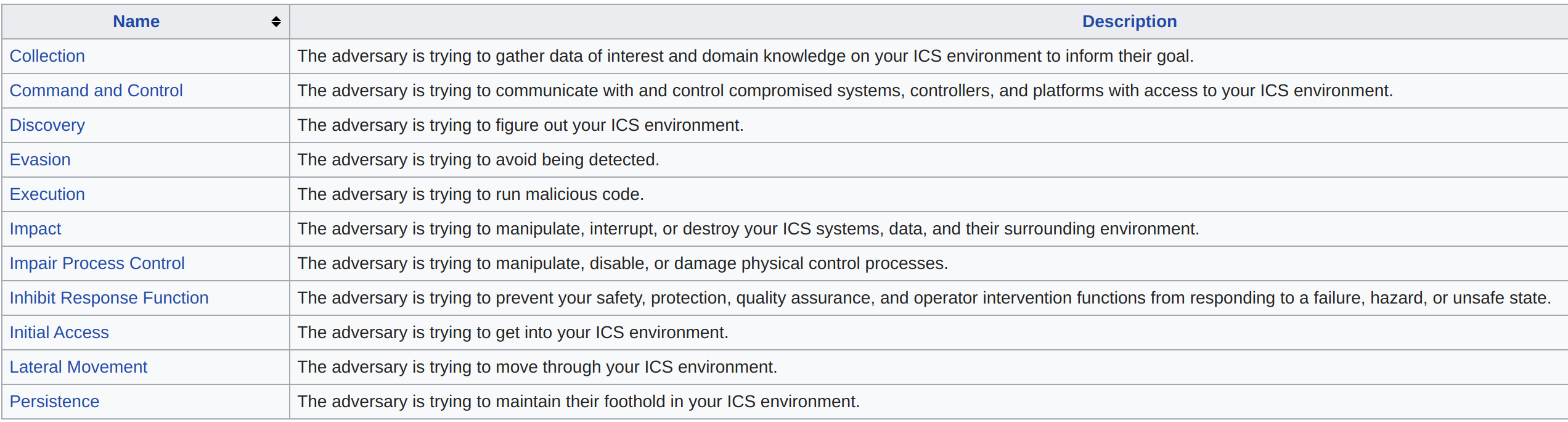
In the following page: https://collaborate.mitre.org/attackics/index.php/All_Techniques you will find the technical description of each of the 81 techniques described in ATT&CK for ICS.
In the second part of this blogpost we will analyse three ICS threats and map their tactics and techniques to the ATT&CK for ICS Matrix.
Do you want to learn more?
We are giving a two-days training about Advanced ICS hacking at Ekoparty and HITB.
Get your tickets!
- HITB (Online РEnglish РSingapore Timezone): https://conference.hitb.org/hitbsecconf2020sin/sessions/2-day-training-2-advanced-ics-hacking/
- Ekoparty (Online РSpanish): https://www.ekoparty.org/eko16/trainings/advanced-ics-hacking-bsas
___________
References and Related Content:
- https://collaborate.mitre.org/attackics/index.php/Technique_Matrix
- https://collaborate.mitre.org/attackics/index.php/Main_Page
- https://collaborate.mitre.org/attackics/index.php/All_Tactics
- https://collaborate.mitre.org/attackics/index.php/All_Techniques
- https://medium.com/mitre-attack/launching-attack-for-ics-2be4d2fb9b8
- https://cyberx-labs.com/blog/telling-the-full-story-with-the-mitre-attck-for-ics-framework/
- https://ics.kaspersky.com/media/ics-conference-2019/12-Marina-Krotofil-If-I-Were-MITRE-ATTCK-Developer-Challenges-to-Consider-when-Developing-ICS-ATTCK-Attacker-perspective.pdf
- https://archive.f-secure.com/weblog/archives/00002718.html
- https://airbus-cyber-security.com/mitre-attck-for-ics-everything-you-need-to-know/


