The most common attack overall is ransomware, although when the environments that provide water, electricity, gas or medicaments are attacked, it can be even more serious, with a direct threat to human lives. Peoples livelihoods depend upon these environments continuing to be fast, effective and most of all, operational. Whilst industrial environments affecting human lives are targeted by nation states or APTs, industrial environments such as manufacturers are targeted by organised crime actors, knowing that they are more likely to pay a ransom in order to restore their operability .
For the vast majority of industrial environments, they must run continually and without any outages, which makes them far harder to take offline for the application of software updates and patches. While IT environments are used to monthly or even more regular patching, Industrial Control Systems (ICS) frequently see quarterly patching as the best case scenario and that contributes to the nearly 50% increase in vulnerabilities in ICS in 2020. The average time for a vendor to release a patch for a vulnerability is 150 days. Adding this 5 months to release a patch to the time to then properly test and deploy it, can mean a minimum of 8 months before a vulnerability is patched even in an ideal scenario.
Another factor why these, often sensitive and life sustaining environments are easy targets is because they can be reliant on outdated systems. Any vulnerability process, even if it exists, is far less flexible due to interoperability issues, system fragility and in many cases the inclusion of completely outdated components, where no further patches are being released. Based on data collected between 2019-2020 from 1,821 production networks - across a diverse mix of industries worldwide - research showed that that 71% of ICS/SCADA sites have outdated Windows systems such as Windows 2000 and XP or Windows 7 that no longer receive security patches from Microsoft[2].
Due to outdated systems and the need for continuous operation, the ICS are both easy and attractive targets for ransomware campaigns all around the world. The main target for ransomware remains the enterprise zone (Level 5 of the Computer Integrated Manufacturing (CIM)/Purdue model), although a worrisome shift in the paradigm emerged in spring 2019 with the MEGACORTEX ransomware, which fortunately seemed to be short lived. Unfortunately, a similar malware named EKANS has been active since the end of December 2019, with both specifically designed to target industrial control systems. The software and hardware used in everything from oil refineries to power grids to manufacturing facilities is on the kill list of processes once the network is attacked. The list of EKANS victims appears to include Bapco, Bahrain's national oil company, private hospital chain Fresenius, multinational energy company Enel and Honda. [4]

Figure 1: CIM/ Purdue Model
It's important to keep in mind that ransomware attacks often use or exploit a number of these weaknesses to compromise the target organization:
- Non-existent Firewalls, incorrectly configured or weak network architecture
- Unnecessary services exposed
- Missing patches for older but critical vulnerabilities
- Lack of validated backups and poor restore processes
- Lack of policies regarding removable media
- Lack of awareness about phishing attempts, and dangerous user downloads
- Insecure or inadequate authentication and access control methods
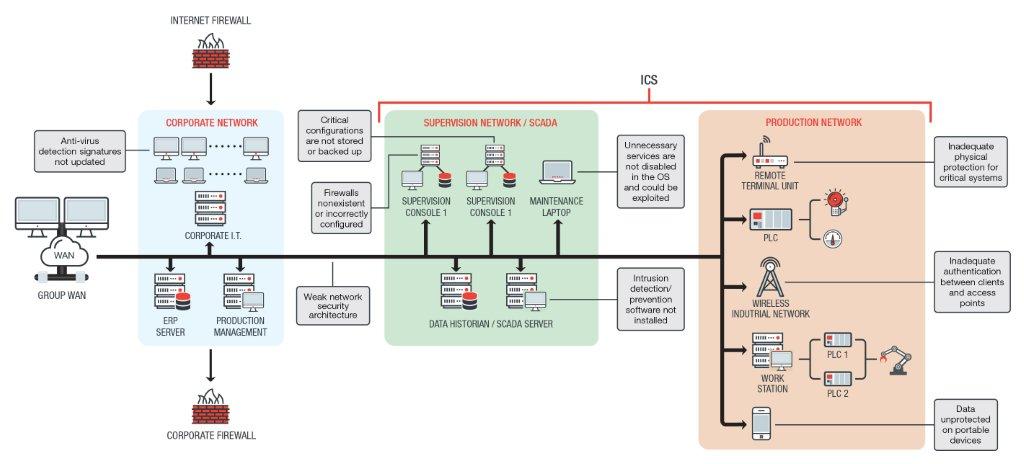
Figure 2: Possible weaknesses in ICS networks
For example, the diagram below shows a scenario in which the WannaCry ransomware penetrates from the corporate to the industrial network, via the workstation of the industrial automation system’s engineer/administrator, which is connected to both the corporate network and the industrial (Operation Technologies) network using two network adapters. [6]
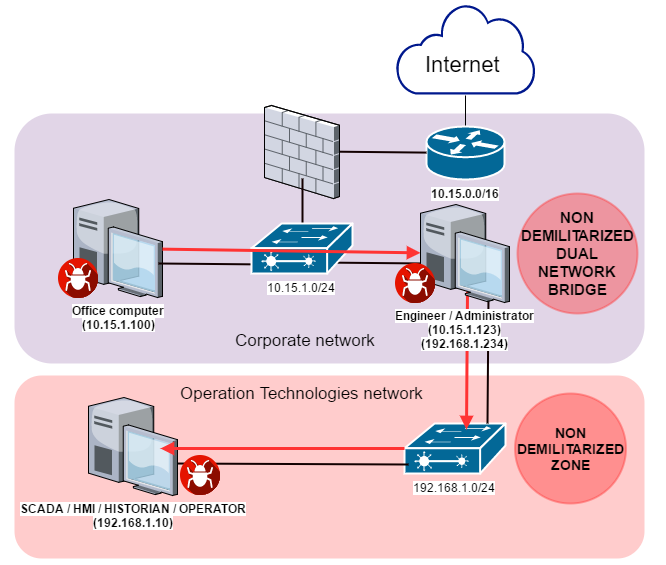
Figure 3: Wannacry Ransomware attacking an OT network
To protect ICS facilities from ransomware attacks such as the ones previously described, a variety of measures or security controls must be taken, knowing that a single security product or technology cannot adequately protect an ICS. Securing an ICS is based on a combination of effective security policies and a properly configured set of security controls. The selection and implementation of security controls to apply to an ICS can have major implications on the operations, so it is critical to consider:
- Which security controls are needed to adequately mitigate risk to an acceptable level to support the organizational missions and business functions?
- Have the selected security controls been implemented or is there a realistic implementation plan in place?
- What is the required level of assurance that the selected security controls are implemented correctly, operating as intended, and producing the desired outcome? [3]
To minimize the risk and impact of a ransomware attack, we recommend taking a set of security controls designed to improve the security of the industrial network:
- Network Segmentation and Segregation: When designing a network architecture for an ICS deployment, it is usually recommended to separate the ICS network from the corporate network. If ICS network traffic is carried on the corporate network, it could be intercepted or be subjected to DoS or Man-in-the-Middle attacks. Also, by having separate networks, security (e.g. ransomware attack) and performance problems on the corporate network should not be able to affect the ICS network. Sometimes a connection is required between the ICS and corporate networks. This connection is a significant security risk and should be protected by boundary protection devices. If the networks must be connected, it is strongly recommended that only minimal connections be allowed and that the connection is through both a firewall and a DMZ (A DMZ is a separate network segment that connects directly to the firewall). Servers containing the data from the ICS that needs to be accessed from the corporate network are put on this network segment, and only these systems should be accessible from the corporate network. With any external connections, the minimum access should be permitted through the firewall, including opening only the ports required for specific communication.
- Smart Patching: Most threats enter through commodity systems such as Windows machines. You cannot and should not patch everything in OT, but a smart patch management program (intelligent application of patches) is of great importance (e.g. critical patches on hosts with RDP or firewalls connected to the Internet should be prioritized over a PLC protected by several layers). So, create a patching plan that works for your process environment and make sure that it includes processes for proper tests and change management controls. Where patching is unfeasible, application whitelisting, and policy enforcement makes an attacker’s life very difficult and improve your chances to defend or deny a ransomware attack on your OT organization.
- Media Protection: The use of any unauthorized CDs, DVDs, floppy disks, USB memory sticks, or similar removable media on any node that is part of or connected to the ICS should not be permitted. These easily transportable and difficult-to-control media can be used to illegitimately collect data from an ICS system and are an important vector for the introduction of malware. There must be clear policies on the use of personal equipment such as laptops, cell phones and wireless routers, since any of these devices once connected to the industrial network represents an attack vector by itself. For these devices, there should be a separate network, completely isolated from the rest of the industrial network architecture. Mechanized policy management software can be used to enforce the media protection policy, in order to block them and reduce the risk of introducing malware or data leakage. If USBs are necessary they must be carefully analysed outside the OT / ICS network before being authorised for use.
- Audit, Monitor and Supervision of ICS systems: The security architecture of an ICS should incorporate mechanisms to monitor, record and audit activities that occur in different systems and networks. Monitoring, logging, and auditing activities are necessary to understand the current state of the ICS, validate that the system is working as intended, and that policy violations and security incidents have not interfered with the operation of the system. They also assist in troubleshooting tasks and in performing any necessary forensic analysis tasks. Monitoring is valuable in understanding the normal state of the ICS and can provide indications of compromised systems. Knowing the normal communications within the environment and monitoring for abnormal use can help detect malicious behaviour that should then be investigated.
- Security Awareness and Training: Personnel are the first line of defence against attack. In ICS / OT environments, operation is paramount, and because people are the most common target of criminals and attackers, it is essential that staff have adequate training to recognize threats and attacks to the operation of the company. The company must identify, document and train all personnel who have important roles and responsibilities in the ICS. Awareness and training should cover both the physical process being monitored, as well as ICS in general. Security awareness is a critical part of ICS incident prevention, particularly when it comes to social engineering threats, phishing and internet downloads.
- Authentication and Access Control: In general, in ICS environments, authentication is carried out through passwords. One problem with passwords in ICS environments is that a user's ability to remember and enter a password can be affected by the stress of the moment. During a major crisis, when human intervention is critically required to control the process, an operator may panic and have difficulty remembering or entering the password and locking the account or delaying responding to the event. In situations where the ICS cannot support, or the organization determines that it is not advisable to implement authentication mechanisms in an ICS, compensatory controls should be used, such as rigorous physical security controls (for example, access card access to the control centre for authorized users) to provide equivalent security capability. Special consideration must be taken when implementing policies based on password authentication within the ICS environment. Some ICS operating systems make it difficult to set up strong passwords, as the password length is short and the system only allows group passwords at each access level, not individual passwords. Some industrial protocols transmit passwords in plain text, which makes them susceptible to being intercepted. In cases where this practice cannot be avoided, it is important that users have different (and unrelated) passwords for use with encrypted and unencrypted protocols. Additionally, users should have different accounts and passwords on the corporate network and on the OT / ICS network. Where possible, a centralized authentication system exclusively for ICS and separate from the corporate one, should be used.
- Backups: Frequent backups of all hosts and ensuring an adequate pipeline to recover systems from those backups, means a faster recovery from any ransomware attack. Offline backups as a disaster recovery strategy are also critical, to ensure that the most important OT assets are protected or can be readily restored if the infrastructure is down. This includes PLC logic code, configuration, documentation, and system images/files.
_______
Do you want to learn more? We are giving a two-days training about Attacking and Securing Industrial Control Systems at HITB in May 2021.
Get your ticket: HITB (Online - English): https://sectrain.hitb.org/courses/attacking-and-securing-industrial-control-systems-ics-may-2021/

Check out also our trainings schedule for more dates: https://dreamlab.net/en/education/trainings-schedule/.
Resources and Related Content:
1: https://newsroom.ibm.com/2021-02-24-IBM-Security-Report-Attacks-on-Industries-Supporting-COVID-19-Response-Efforts-Double, IBM, 2021
2: https://cyberx-labs.com/resources/risk-report-2020, CyberX,2020
3: https://csrc.nist.gov/publications/detail/sp/800-82/rev-2/final
5: Figure 1: https://medium.com/shellpwn/introduction-to-industrial-control-system-4935ad1a1db6
6: Figure 3: https://ics-cert.kaspersky.com/reports/2017/06/22/wannacry-on-industrial-networks/
7: Figure 2: https://www.trendmicro.com/vinfo/us/security/news/cyber-attacks/why-do-attackers-target-industrial-control-systems
___________
Sarka Pekarova
Security Consultant at Dreamlab Technologies
Yamila Levalle
Security Researcher at Dreamlab Technologies

